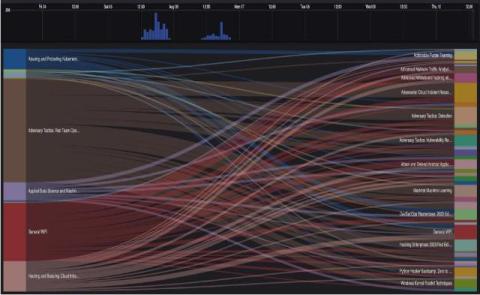
Gartner Report: Implement a Continuous Threat Exposure Management (CTEM) Program
According to Gartner, “By 2026, organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach.” But what exactly is CTEM?