Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Data Security
The latest News and Information on Data Security including privacy, protection, and encryption.
Encrypting files and emails: A beginner's guide to securing sensitive information
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In today's digital age, sensitive information is constantly being shared and transmitted over various electronic devices and networks.
Updated Cato DLP Engine Brings Customization, Sensitivity Labels, and More
Last year, we launched Cato DLP to great success. It was the first DLP engine that could protect data across all enterprise applications without the need for complex, cumbersome DLP rules. Since then, we have been improving the DLP engine and adding key capabilities, including user-defined data types for increased control and integration with Microsoft Information Protection (MIP) to immediately apply sensitivity labels to your DLP policy. Let’s take a closer look.
Freedom to Innovate: Data Privacy Methods
How do Cloud Access Security Brokers (CASBs) Work and Should I Use One?
As organizations increasingly adopt cloud services and applications, securing access to these services becomes crucial to protect sensitive data and maintain compliance. Cloud Access Security Brokers (CASBs) have emerged as a key component in providing comprehensive visibility and control over cloud services.
Defining Your Organization's Attack Surface: The 4 Types of Attack Surfaces
Attack surfaces are a fundamental concept within information security. However, attack surfaces can be constituted of different things. For example, some formulations of an attack surface include not just software and hardware, but the people using them. In this post, we’re going to cover four common types of attack surface, discuss how you should think about the risks associated with each type, and best practices for addressing these risks.
How to Establish Cross-Border Transfer Systems that Help Protect Privacy
Cybersecurity, privacy and data flows will be key topics at this year’s G7 in Japan. Against this backdrop, it has been a year since last year’s amendments to the Act on Protection of Personal Information (APPI) introduced revised data breach reporting and cross-border data flow rules. Meanwhile, developments in the Asia-Pacific (APAC) region have introduced data localization obligations in a variety of countries.
Top 10 ways to secure Ruby on Rails applications
Ruby on Rails is one of the most loved combinations in tech. It’s a language and framework that’s accessible to people of varying skill sets and experience. Its maturity and widespread adoption shows with how much the core team and community care about security. Each release improves the framework's hardiness, but there's still so much we can do as developers to protect our applications.
Data Encryption At Rest vs In Motion in Microsoft 365
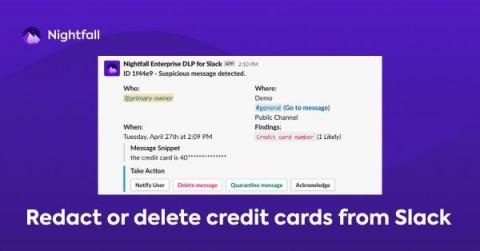
How to Prevent Credit Card Number Exposure in Slack for PCI Compliance
For many companies, a business credit card is part of the organization’s lifeblood. As such access to it must be vigilantly maintained. One potential area of risk is employees sharing credit card details in collaborative SaaS applications like Slack, where these details are at significant risk of being exposed to unauthorized parties.