Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Ruby
The Unseen Risks of Open Source Dependencies: The Case of an Abandoned Name
One often-overlooked risk in the bustling ecosystem of open-source software are vulnerabilities introduced through software dependencies. We mention this because today, a malicious actor took over a RubyGems package name with more than two million downloads. Mend.io technology detected the package before it could be used for an attack, but the case of ‘gemnasium-gitlab-service‘ serves as an important reminder of the risk of neglecting dependency management.
Finding YAML Injection with Snyk Code
I conducted some research to try and identify YAML Injection issues in open-source projects using Snyk Code. Though the vulnerability itself is not a new one, the potential impact of YAML Injection is high, which made it a good candidate for research. This research led to the discovery of several issues in open-source projects written in Python, PHP and Ruby. This article focuses on the issue found in geokit-rails version 2.3.2, a plugin for Ruby on Rails
Ruby on Rails Docker for local development environment
Hi there Ruby developers! If you’ve been looking for an effective way to establish a Ruby on Rails Docker setup for your local development environment, then this post is for you. It’s a continuation of our previous article on how to install Ruby in a macOS for local development. Ruby developers frequently need to account for a database when building a Ruby on Rails project, as well as other development environment prerequisites.
To use rest_client, or to use rest-client, that is the question
Rest-client is one of the most popular RubyGems, with a simple DSL that allows sending HTTP requests. Lightweight, versatile, developed by famous Rubyists…with all these attributes, this gem is a very shiny and attractive target for malicious actors. All they need is a good method of attack. An attempt made today tried to leverage typosquatting by adding malicious code to rest_client, but it didn’t quite ace the assignment.
Ruby email rule removed from Snyk Code
Snyk Code supports various languages important in the cloud native arena, Ruby being among them (and we’ve seen great adoption, so thank you!). Our researchers are constantly monitoring our rule sets, using our training set of open source projects, but also — and, yes this is an advantage of a SaaS service — how the rules do on the code that is scanned. Just as a reminder, Snyk does not use your code to train our sets — but we do aggregate usage statistics.
Ruby gem installations can expose you to lockfile injection attacks
In this post, we’ll look at the security blindspots of lockfile injection that a Ruby gem might expose via its Gemfile.lock. As a prelude to that, we will open up with a brief introduction to Ruby and third-party dependencies management around RubyGems and Bundler. Web developers often work on Ruby projects, but are mostly referring to them as the popular open source web application framework Ruby on Rails.
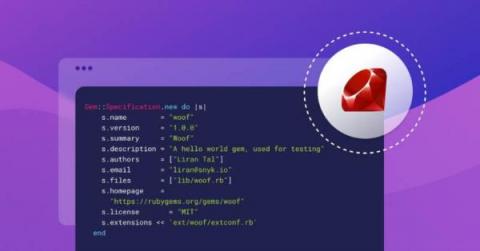
A definitive guide to Ruby gems dependency management
Ruby, much like other programming languages, has an entire ecosystem of third-party open source libraries which it refers to as gems, or sometimes Ruby gems. These gems are authored by the community, and are available from RubyGems.org which is the official registry for Ruby libraries. Similarly to other open source ecosystems, threat actors may publish deliberate malicious code or such which includes backdoors or credentials harvesting.
Impact Analysis: CVE-2022-29218, Allows Unauthorized Takeover of New Gem Versions via Cache Poisoning
It’s been a bad month for RubyGems vulnerabilities. Critical CVE-2022-29176 was issued May 8, 2022, and another critical CVE-2022-29218 was discovered less than a week later, on May 11. This new vulnerability would allow for a takeover of new versions of some platform-specific gems under certain circumstances.
Impact Analysis: RubyGems Critical CVE-2022-29176 Unauthorized Package Takeover
On May 6, 2022, a critical CVE was published for RubyGems, the primary packages source for the Ruby ecosystem. This vulnerability created a window of opportunity for malicious actors to take over gems that met the following criteria: Because RubyGems provides data dumps that include a lot of information, it is unfortunately relatively simple to create an automated mining process for these criteria.