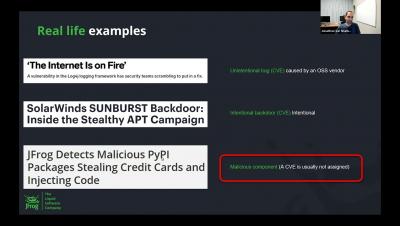
A Simple Guide to Getting CVEs Published
We were once newcomers to the security research field and one of the most annoying problems we ran across was how to get a CVE published. After all, what good is it to find a juicy vulnerability if you can’t get the word out to others? So, as a resource to help our fellow researchers, we decided to put together a CVE publishing guide based on our experience, and honestly a lot of good old trial and error.