Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Access Management
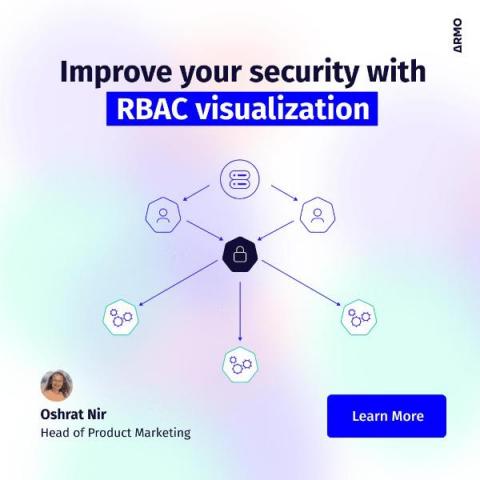
Visualizing RBAC for Improved Security Management and Outcomes
Securing the Public Sector: How to Modernize ICAM Solutions
The Technology Modernization Fund’s (TMF) latest awards targeting cybersecurity, zero trust, and classified cloud highlight the increasing importance of modernizing the federal government’s IT infrastructure to combat emerging cybersecurity threats.
The hazards of not using just-in-time (JIT) privileged access in Active Directory
Active Directory (AD) is the foundation of managing identities, provisioning users and issuing permissions to network resources. These permissions range from the lowest levels of access to the highest levels of admin rights for privileged users. While having control over these permission levels is useful, organizations can open themselves up to serious vulnerabilities if they don’t manage the permission levels carefully.
Unveiling the Bank Security Secrets: How CIAM and Identity Verification enable seamless Onboarding
Due to the importance of its data, frequent audits, and the fines and financial implications of fraud, the banking and financial services sector is subject to some of the most stringent rules and monitoring in existence today. Technology platforms, procedures, and policies that guarantee your organization’s compliance and security are essential to keeping ahead in the banking industry in the digital era.
PAM Masterclass - Episode 1: Streamlining privileged account governance
DevSecOps - Why, When & How?
OneLogin and AWS CloudTrail Lake Integration
As an AWS Partner, One Identity is proud to announce that it is now even easier to leverage your existing AWS tooling with your OneLogin data. We are among the first partners to offer a new integration that joins tools, such as our previously released AWS EventBridge webhook. Now, AWS and One Identity have teamed to deliver an integration with AWS CloudTrail Lake, which allows you to store your OneLogin event data in AWS along with all your other data.
Introducing SSH command controls and advanced PEDM capabilities for Linux in PAM360
PAM360 is ManageEngine’s comprehensive privileged access management (PAM) solution designed for enterprises to protect sensitive, privileged identities from internal and external threats. With the principle of least privilege enshrined across the product, PAM360’s privilege elevation and delegation management (PEDM) capabilities help enterprises eliminate standing privileges and provide granular privileged access in a restricted, time-based manner.