Check out Apono on Okta Marketplace: https://www.okta.com/integrations/apono/
- January 2025 (2)
- December 2024 (3)
- November 2024 (3)
- October 2024 (3)
- September 2024 (1)
- August 2024 (3)
- July 2024 (4)
- June 2024 (4)
- May 2024 (5)
- December 2023 (1)
- November 2023 (3)
- October 2023 (2)
- September 2023 (5)
- May 2023 (1)
- March 2023 (1)
- February 2023 (2)
- January 2023 (1)
Securely manage permissions and adhere to compliance requirements, while allowing employees to benefit from a frictionless user experience.
Apono, led by cybersecurity and DevOps experts. “Apono” is the Hawaiian word for “approve”. The Apono platform is loved by DevOps, trusted by Security - supports customers like OpenWeb, Cybereason, HiredScore, Tomorrow.io and many more in automating permission management. Providing a frictionless experience for users with the visibility and compliance needed by security to win more business.
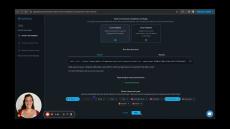
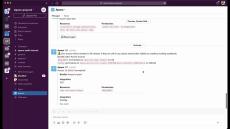
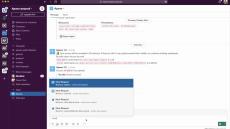
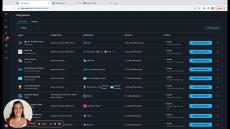
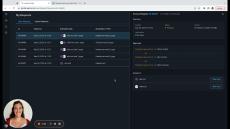
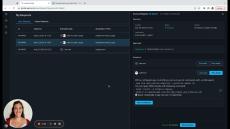
Turn Manual Permission Management Into Automated Contextual Access Flows:
- Remove Permission Bottlenecks: Turn manual permission management tasks to automated contextual Apono Access Flows.
- Leave No Permissions Behind: Take advantage of auto-expiring permissions.
- Satisfy Customer Requirements: Grant access to specific namespaces or resources with a comprehensive audit log.
- Prevent Human Errors in Production: Tailor access duration and resources to the task at hand.
Automatic granular permissions needed to keep your business running and secure.