Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
What is Reverse Proxy, How Does It Work, and What are Its Benefits?
CISA Publishes Advisory on Improving Network Monitoring and Hardening
CISA released in late February a cybersecurity advisory on the key findings from a recent Cybersecurity and Infrastructure Security Agency (CISA) red team assessment to provide organizations recommendations for improving their cyber posture. According to the Agency, the necessary actions to harden their environments include monitoring network activity to spot abnormal behavior, conducting regular assessments and drills, and enforcing phishing-resistant MFA anywhere possible.
Introducing the Industry's First Unified, All-Software SASE Client with Integrated Netskope Endpoint SD-WAN and Intelligent SSE
There exists a drive in all of us that embraces innovation to make life easier. For IT leaders, it’s time for true innovation at the remote access edge.
AlgoSec - a single solution to secure application connectivity and accelerate policy changes
What is SD-WAN? | SD-WAN Explained #sdwan
Cloud WAF Pricing: All You Need to Know
Where Insider Threats Hide Out in a Segmented Network
Three Ways VPNs Make Remote Access Less Secure
Virtual private networks (VPNs) were introduced roughly two decades ago with the idea that creating an encrypted tunnel directly from a computer device to a network would provide secure access to company resources and communications from remote locations. VPN performance was notoriously sluggish, and they were difficult and time consuming for IT to administer, but at least the appliances were secure. Or so people thought.
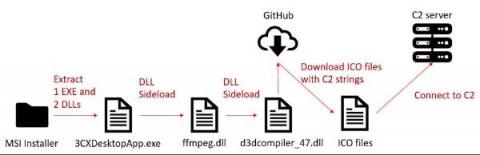
How to Detect and Mitigate the 3CXDesktopApp Supply Chain Attack
On March 29, researchers from two security companies identified an active campaign originating from a modified version of a legitimate, signed application: 3CXDesktopApp, a popular voice and video conferencing software. 3CXDesktopApp is developed by 3CX, a business communications software company. According to its website, 3CX has 600,000 client organizations and 12 million daily users.