Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Malware
Royal Mail Ransomware Attack - Part 2
Following on from part 1 of our Royal Mail blog, our consultants take a more technical approach to the Royal Mail Ransomware attack and dive deeper into what happened.
Cyber Trends for 2023: The Bots are Still Coming, but Humans are Driving Them
If one topic has been on the minds of CISOs and CIOs alike over the last three years of Covid and post-Covid hybrid enterprise work environments, it’s ransomware. A distributed tech workforce — using distributed software services — proved to be no match for highly automated ransomware bots and malware executing encryption attacks. But this year, like the end of War of the Worlds, the attacking bots may suddenly fall silent.
Rubrik Recognized as a 2023 Customers' Choice for Enterprise Backup and Recovery Software Solutions on Gartner Peer Insights
Rubrik is on a mission to secure the world’s data. And our customers are at the very heart of that mission. Research from Rubrik Zero Labs’ State of Data Security report found 98% of global IT and cybersecurity leaders dealt with a cyberattack in the last year, exposing just how critical it is for businesses to have a solid data security strategy in place and a platform they can trust to protect against these ever-growing cyber threats.
Detecting Malicious Packages and How They Obfuscate Their Malicious Code
Wow! We made it to the last post in our Malicious Packages series. While parting is such sweet sorrow, we hope blogs one, two, and three provide insights into the havoc malicious packages cause throughout your DevOps and DevSecOps pipelines. In the prior posts: Now let’s get to know attackers’ other, more discreet interests when creating a malicious package: hiding malicious code, and finally showing how malicious packages can be detected and prevented.
The Simply Cyber Report: January 30, 2023
Covenant C2 Fills the Void Left by Empire PowerShell
Post-exploitation tools are used by threat actors to move laterally inside a network and escalate their privileges in order to steal data, unleash malware, create backdoors and more. Red teams and ethical hackers also use these tools; indeed, simulating the efforts of adversaries plays a key role in implementing effective controls to secure systems, applications and files.
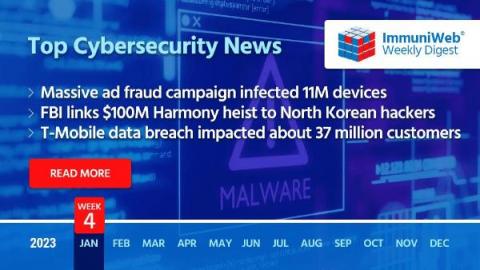
Massive Ad Fraud Campaign Infected 11M Devices, Spoofed 1,700 Apps and 120 Publishers
Read also: PayPal, Riot Games compromised, FBI links $100M Harmony hack to North Korea, and more.
How Did Kaseya Get Hacked?
The Kasya ransomware attack occurred through the exploitation of CVE 2021-30116, an authentication bypass vulnerability within Kaseya VSA servers. This allowed the hackers to circumvent authentication controls and executive commands via SQL injection, giving them all the control they needed to deploy their ransomware payload and encrypt a segment of Kaseya's internal data.
CTI Roundup: Ransomware Profits Drop as Attacks Remain High
Reporting revealed declining ransomware profits in 2022, a new backdoor based on the CIA’s Hive malware is discovered, and a new wave of BackdoorDiplomacy attacks are targeting Iranian government entities.