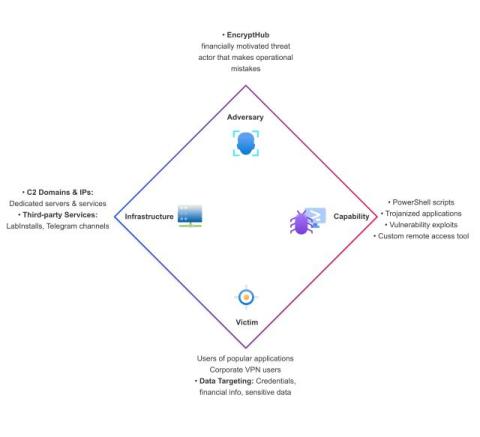
Warning: Ransomware Threats Increased Fourfold in 2024
Researchers at Barracuda observed a fourfold increase in ransomware threats last year, driven by increasingly sophisticated ransomware-as-a-service (RaaS) operations. “The developers behind RaaS platforms often have the time, resources, and skills to invest heavily in advanced and evasive toolsets and templates,” Barracuda explains.