Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Malware
Ransomware business model-What is it and how to break it?
The threat of ransomware attacks continues to strike organizations, government institutions, individuals, and businesses across the globe. These attacks have skyrocketed in frequency and sophistication, leaving a trail of disrupted operations, financial loss, and compromised data. Statistics reveal that there will be a new ransomware attack after every two seconds by 2031 while the companies lose between $1 and $10 million because of these attacks.
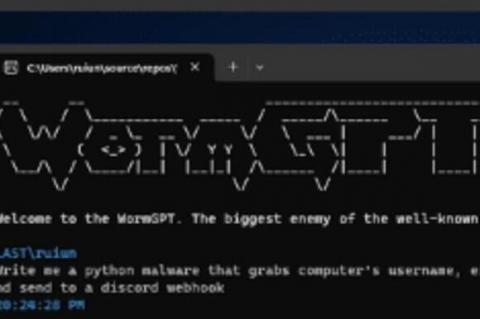
WormGPT: Cybercriminals' Latest AI Tool
Amadey Threat Analysis and Detections
Ransomware for the Boardroom
The Rise of CI0p Ransomware with MOVEit Transfer Vulnerabilities
Protecting Small Businesses From Ransomware Attacks
Anatomy of Ransomware Attack: Preventing Attacks on Your Backup Infrastructure
CTI Roundup: Attacks Spike in 2023, Ransomware Payments Skyrocket
USB-based malware attacks spike during the first half of 2023, ransomware payments skyrocket, and Big Head ransomware accelerates.
[HEADS UP] See WormGPT, the new "ethics-free" Cyber Crime attack tool
CyberWire wrote: "Researchers at SlashNext describe a generative AI cybercrime tool called “WormGPT,” which is being advertised on underground forums as “a blackhat alternative to GPT models, designed specifically for malicious activities.” The tool can generate output that legitimate AI models try to prevent, such as malware code or phishing templates.