Ransomware in the Global Healthcare Industry
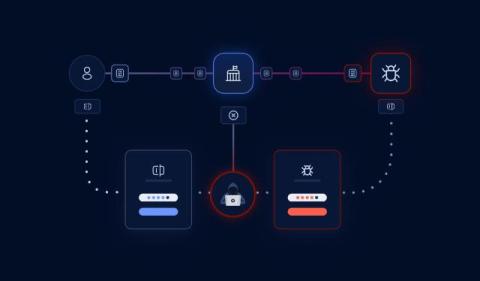
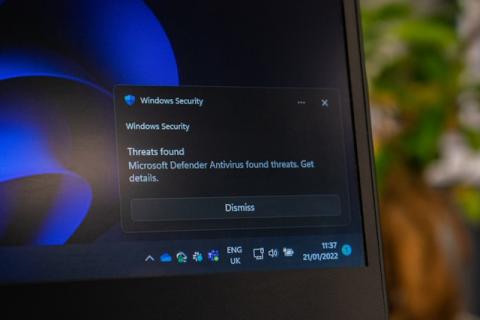
The World Health Organisation (WHO) recently hosted a webinar to discuss the critical importance of cybersecurity in the healthcare sector, which highlighted the severity of the situation the industry is currently facing. Healthcare organisations are increasingly relying on digital systems to facilitate their daily workflow, but the prevalence of outdated legacy technology in the sector is rendering it vulnerable to cyberattacks with severe consequences.