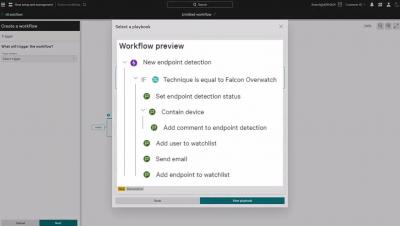
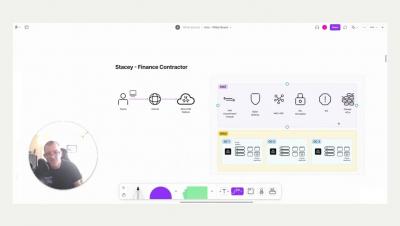
As DevOps turns to multi-cloud, workload containerization, and infrastructure-as-code, securing and distributing secrets across teams and environments has become a complex undertaking. Left unmanaged, this leads to secrets sprawl; in other words, the exposure of credentials in source control servers, DevOps tools, and every component that makes up the software development life cycle (SDLC). With exposed secrets, attackers can easily access an organization’s critical resources. They can breach the perimeter to carry out attacks, hijack computing power, exfiltrate customer data and compromise the integrity of the software supply chain.