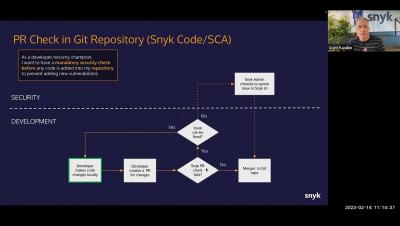
Snyk Workflows - Ignores & PR Checks
Snyk integrates with your IDEs, repos, workflows, and automation pipelines to add security expertise to your toolkit. The “menu” of options available to you is extensive, so we created this three-part series to get you started and running. Do you want your dev teams and AppSec teams to be aligned? The second session of the series digs deeper into using ignore capabilities. You’ll also learn about PR checks. This is a great way to get ahead of permissions.