|
By Ann-Anica Christian
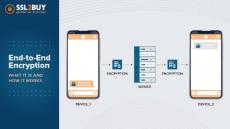
You might have visited a website and seen a warning that says: “Your connection is not private.” This often happens when a website’s security certificate has expired. It is a small oversight that can harm a website’s reputation and make visitors think twice before proceeding. For website owners, managing digital certificates manually can be a real challenge. To simplify this process, the ACME Protocol was developed.
|
By SSL2BUY
Spear phishing plays a significant role in causing data breaches and cyberattacks. It costs businesses and individuals millions of dollars each year. Spear phishing is different from traditional phishing, which covers a broad spectrum. It targets specific individuals or organizations and uses tricks to make the victim reveal some sensitive information. This article explores spear phishing. It covers its unique traits and offers expert tips to identify and stop such attacks.
SSL/TLS cipher suite is a collection of cryptographic algorithms that collaborate to enable Secure sockets layer/Transport layer security (SSL/TLS) Protocols. This article explains how a cipher suite provides secure, encrypted online communication. Let’s dive in!
Data backup is an important part of cybersecurity. Implementing appropriate data backup solutions may save both time and money. Understanding and adhering to current backup procedures is critical, as is partnering with IT workers. Imagine an organization experiencing a sudden hardware failure on their computer. Without proper backups, restoring critical records gets delayed or even impossible. If there is no backup policy in place, one must be created.
Artificial Intelligence is a game-changer technology that has created a buzz in today’s market, which we believe you can agree on. How has AI become a game changer in such a short span of time? Well, the hype is real, and it is because of the revolutionary tools and technologies that come into the market. That’s the one side of the coin! What about the other side? Yes, with these modern AI technologies, there is a fear which we overlooked and that’s security.
The Internet is experiencing a new wave of virtual experience, named Metaverse. As the internet grows, users are getting more interested in immersive experiences in terms of gaming, shopping, and buying virtual assets. The Metaverse lets millions of people build new interactions and digitally recreate ones that are more like the real world. According to recent statistics, the Metaverse market is expected to reach $74.4 billion by 2024.
In an advanced interconnected world, the internet is essential in facilitating a significant portion of communications, making security a paramount concern. Whether you pick up a newspaper or follow a news link, you will see reviews of some other protection breach or hacking try. Despite the inherent risks associated with online communication and data exchange, the speed and convenience of technology make it a worthwhile endeavour. However, there is a strategy to address these concerns.
Digital identity is becoming important these days. Whether for online banking, online shopping, or dealing with government officials, digital identity helps you to perform transactions securely online. On the other hand, conventional authentication methods are reaching their limit regarding maintaining security. However, technological advancements have paved the way for advanced approaches to user identification. This advancement adds to the advanced rules, laws, and regulations in the European Union.
An Insider Threat is a risk that can cause individuals with access to an organization’s systems, networks, or data to exploit that access for a malicious purpose. This threat can be caused by employees, contractors, business associates, or anyone with authorized access to assets of the organization.
IPsec is a set of Internet Protocols offering secure connection between devices. It is generally used by Virtual Private Networks for encrypting IP packets and authenticating the sources.
|
By SSL2BUY
Our happy client is a budding programmer. For the program he was working on, he wanted to ensure the finest downloading experience for his clients. This led him to #SSL2BUY where he found the best deals on well-known Code Signing Certificates. SSL2BUY client was very pleased with the services. Moreover, he was able to find the best Code Signing certificate thanks to the smooth order and payment process and industry-leading customer assistance.
|
By SSL2BUY
SSL2BUY is well-known for its best customer service and lowest SSL certificate prices. Jordy has again proved it by posting his feedback. With the purchase of a Code Signing Certificate, he does not only get the best prices but also fabulous after sales support.
|
By SSL2BUY
One of #SSL2BUY customer Ilker Gulener from Turkey shares their personal review about our customer service.
|
By SSL2BUY
Hello. My name is Sue Melina running a travel agency, a travel agency in Peru Puna. And in my side, I need an #SSLcertificate for my customers to purchase online. Thank you again. So and if you want to purchase an #SSL certificate, you can trust with them.
|
By SSL2BUY
He is very surprised to see how the whole process of buying and implementing an #SSL Certificate went smooth and straight forward,Also he was very satisfied with the price. Check out the video in which he is sharing his experience and feedback..
|
By SSL2BUY
SSL2BUY's customer is very satisfied with our products and services. He is very pleased the way our customer support helped him with his confusion with #SSLCertificates. He shared his personal experience with #SSL2BUY, Check it out.
|
By SSL2BUY
#SSL aka Secure Sockets Layer is also known as Digital Certificate, create a secure path between the customer and a website. SSL Encryption makes sure that the information passed between the customer and a website should remain secured.
- January 2025 (1)
- December 2024 (1)
- September 2024 (1)
- July 2024 (1)
- February 2024 (3)
- January 2024 (1)
- December 2023 (2)
- October 2023 (1)
- September 2023 (1)
- August 2023 (2)
- July 2023 (2)
- June 2023 (1)
- May 2023 (1)
- April 2023 (1)
- March 2023 (1)
- February 2023 (2)
- January 2023 (1)
- December 2022 (1)
- November 2022 (2)
- October 2022 (2)
- September 2022 (1)
- August 2022 (1)
- July 2022 (2)
- June 2022 (3)
- May 2022 (2)
- April 2022 (1)
- June 2021 (1)
- October 2020 (1)
- July 2020 (1)
- March 2020 (1)
SSL2BUY delivers highly trusted security products from globally trusted top 5 Certificate Authorities. The digital certificates available in our store are trusted by millions – eCommerce, Enterprise, Government, Inc. 500, and more.
Benefits of SSL/TLS Certificates:
- Strongest SSL Encryption: SSL protect online transactions with strong 256-bit SSL encryption. We offer low-cost SSL, but never compromise with your web security. Our all SSLs come with modern algorithms recommended by the CA/Browser forum.
- Avoid Browser’s Warnings: Browsers have started to show an insecure warning on non-HTTP sites. Customers will quickly move from the site, which shows an insecure warning. It is the best time to get an SSL certificate if you have not purchased it yet.
- Boost Search Rankings: Google added HTTPS as part of their search ranking algorithms, and they will give higher positions in search results for HTTPS secure sites over HTTP non-secure sites. Don’t wait until it’s too late, get better rankings with our inexpensive SSL certificates.
- Protect Personal Data: Customers are aware about the security of their private information and prefer to shop from HTTPS secure sites. So, go through the purchase process and choose a 2048-bit key length to provide a secure environment to your customers.
- Increase Visitor’s Trust: SSL allows visual signs “HTTPS” before your domain name, so users can easily trust on your secure site. Once you purchase SSL from us, you will get “Secure Seal” at free of cost. It will help to get the assurance of customers.
- PCI Compliance: PCI-DSS compliance requires to have an HTTPS security on a website that deals with customer’s online credentials and payment. In the case of averting eavesdropping and MITM attacks, SSL security plays an important role and keeps cyber thieves away from the online information.
Get hassle-free security solutions with our low-cost SSL certificates.