Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
A Step-By-Step Guide to Creating a Risk Register (Template included!)
Running a business is full of surprises. Unexpected events can pop up at any time, potentially leading to the derailment of your organization’s goals. If everything suddenly went haywire, would you and your team know what to do in the heat of the moment? That’s precisely why having a robust risk management program is crucial, and it all starts with a risk register – a tool used to identify and mitigate potential problems.
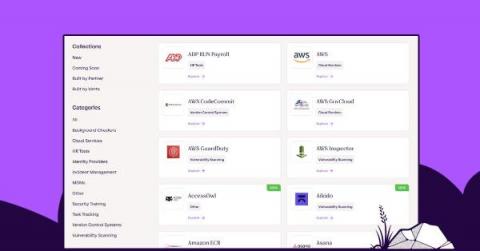
Vanta delivers over 50 new integrations in one quarter
We’re thrilled to announce that we’ve delivered more than 50 new system integrations over the past quarter, taking us to a total of 110 integrations. This is far ahead of any other automated compliance solution in the market, reflecting our innovation velocity and long-term commitment to ensuring customer value and success with Vanta.
Mobile Money Compliance: The Importance of AML Screening in 2023
Anti-money laundering (AML) compliance in the mobile money industry has become increasingly important in 2023. With the rise of mobile money transactions, regulatory bodies are ramping up efforts to combat money laundering and terrorist financing. In this infographic, we explore the technology involved in AML screening, the importance of AML compliance in the industry, and best practices for financial institutions.
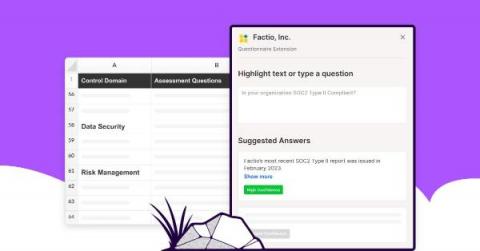
Introducing Questionnaire Automation
Following our recent acquisition of Trustpage, we are excited to announce Questionnaire Automation, a solution designed to help organizations in quickly responding to security questionnaires and effectively communicating security and compliance to customers and prospects. This solution utilizes the fastest and most accurate automation technology to provide security questionnaire responses.
SOC 1, 2, 3 Compliance: The 2023 Guide to Understanding & Achieving SOC Compliance
What is SOC 2 and how do you achieve SOC 2 compliance for containers and Kubernetes?
SOC 2 is a compliance standard for service organizations, developed by the American Institute of CPAs (AICPA), which specifies how organizations should manage customer data. SOC 2 is based on five overarching Trust Services Criteria (TSC): security, availability, processing integrity, confidentiality, and privacy. Specifically, the security criteria are broken down into nine sections called common criteria (CC).
The ISO/IEC 27001 Standard for InfoSec: Meaning, Importance & Requirements
FedRAMP Compliance: What It Is, Why It Matters & Tips for Achieving It
Strengthening CJIS Compliance with Keeper Security: Protecting State Agencies and Law Enforcement
In November 2022, the Criminal Justice Information Services (CJIS) division of the FBI updated its cybersecurity policy, impacting state agencies, police departments, and other organizations that handle Criminal Justice Information (CJI). The updated policy poses challenges for organizations, especially smaller ones, to maintain compliance due to limited resources, lack of expertise and the policy’s complexity.