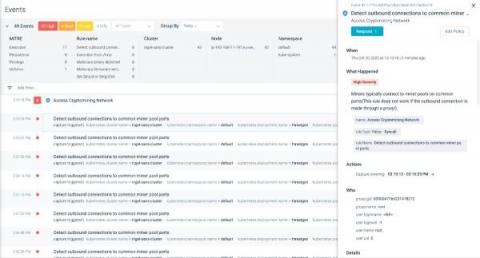
Detecting Cryptomining Attacks "in the Wild"
Cryptomining attacks are becoming more notable in-line with the rise of blockchain and cryptocurrencies, so detecting cryptomining has become a high priority. Security researchers have found data breaches related to various cryptominer binaries running within victims’ infrastructures. The default openness of Kubernetes clusters and the availability of the extensive compute power required for mining makes Kubernetes clusters a perfect target for cryptomining attacks.