Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Cyberattacks
What is DLL hijacking? The Windows exploit endangering your sensitive data.
A simple DLL file was the catalyst to the most devastating cyberattack against the United States by nation-state hackers. This cinematic breach demonstrates the formidable potency of DLL hijacking and its ability to dismantle entire organizations with a single infected file. DLL hijacking is a method of injecting malicious code into an application by exploiting the way some Windows applications search and load Dynamic Link Libraries (DLL).
SolarLeaks
In the aftermath of the notorious SolarWinds breach, occurring in mid-December 2020, a nefarious website was observed on 12 January 2021 and, presumably linked to the threat actors involved in the original supply chain attacks, purports to offer stolen data from four victim companies for sale: Other than the above, no file listings, screenshots or detailed 'proof' have been provided although links to four encrypted archive files, one for each potential victim organization, were uploaded to the popular
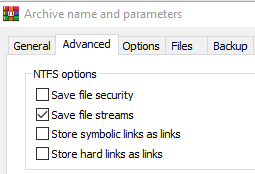
Exploring NTFS Alternate Data Streams from a security standpoint
In this blog we will explore several ways that Alternate Data Streams (ADS) are abused by attackers to hide files and evade detection, defences based on them (and ways to bypass those defences!) but also how they can be used to help malware evade dynamic analysis.
Olivier Trupiano (Founder of Signalement) Reviews Astra's Security Audit & VAPT
Why cybersecurity awareness is a team sport
Cybersecurity may be different based on a person's viewpoint. One may want to simply protect and secure their social media accounts from hackers, and that would be the definition of what cybersecurity is to them. On the other hand, a small business owner may want to protect and secure credit card information gathered from their point-of-sale registers and that is what they define as cybersecurity.
4 Most Common Types of Cybersecurity Threats
There's every indication that the pandemic is changing the nature of cybersecurity. Online threats are evolving to match our new remote-work paradigm, with 91% of businesses reporting an increase in cyberattacks during the coronavirus outbreak. Hackers are getting more and more sophisticated and targeted in their attacks. Many of these cyber threats have been around for a while, but they are becoming harder for the average user to detect. Beware of these four common types of cyber threats - and learn what you can do to prevent them.
Why are cybercriminals suddenly targeting maritime infrastructure?
If you were asked to list out the top problems society has been facing in 2020, cyberattacks on the maritime industry might not be an obvious issue that would come to mind. But the industry has seen a worrying trend in recent months, as a spike in cyberattacks that has left some of the biggest companies in the industry exposed. Specifically, both the fourth largest global shopping company and the International Maritime Organization (IMO) have been targeted in these attacks.
The Biggest Cyber Attacks and Tips to Build Cyber Resilience
What is a supply chain attack (and how to prevent it)
In December 2020, the U.S government announced that it fell victim to what is believed to be the largest security breach in the nation's history. The breach occurred through an innocuous IT update from the Government's network monitoring vendor, SolarWinds. This monumental breach exposes a novel and powerful method of clandestinely penetrating even the most sophisticated security defenses through third-party vendors - supply chain attacks.