- December 2024 (1)
- November 2024 (1)
- September 2024 (1)
- August 2024 (1)
- July 2024 (2)
- June 2024 (4)
- February 2024 (1)
- November 2023 (1)
- October 2023 (1)
- July 2023 (4)
- June 2023 (1)
- April 2023 (1)
- March 2023 (4)
- December 2022 (1)
- November 2022 (2)
- October 2022 (1)
- August 2022 (2)
- June 2022 (1)
- May 2022 (1)
- March 2022 (2)
- February 2022 (1)
- January 2022 (7)
- December 2021 (1)
- November 2021 (1)
- August 2021 (4)
- June 2021 (1)
- May 2021 (5)
- March 2021 (2)
- February 2021 (3)
- January 2021 (3)
- December 2020 (3)
- November 2020 (1)
- August 2020 (2)
- July 2020 (1)
- June 2020 (1)
- May 2020 (1)
- April 2020 (1)
- February 2020 (1)
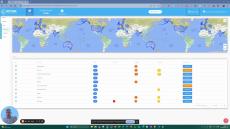
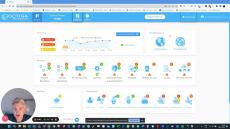
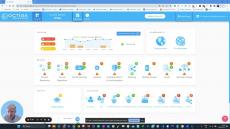
Octiga is a true SaaS solution, born in cloud. It helps you identify security risks and guides you to properly configure your security posture. Our services alert you to suspicious incidents as they occur as well as risky configurations in your Microsoft Office 365 tenant. Our affordable, automated and effortless cyber security monitoring and auditing services are designed by cybersecurity experts with many years of industry experience.
Octiga’s intelligent algorithm looks out for risks in real-time to provide you with instant notification and remediation solutions. Our product is fully cloud-based and simply requires an online sign in using your Microsoft 365 account. From there, you can use the following features to complete your security journey.
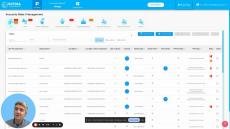
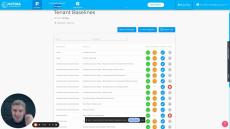
- Prevent: This feature benefits anyone who is responsible for Office 365 security configuration and remediation. Octiga tailors the security configurations to fit an organisation’s unique usage and compliance needs. Its guided wizard ensures that each user is able to automate the configurations in a streamlined and hassle-free way. Octiga’s Office 365 multi-tenant administration scans your entire Office 365 instance, highlights issues and guides you through a series of best practices to achieve safe and secure operation. It addresses not just safe configuration but also safe user account access and management, sharing, and all the other potential weaknesses that may have escaped your attention.
- Detect: Octiga acts as a watchdog for risks and threats, looking over suspicious user activity and configuration changes round the clock. Our intelligent algorithms, in conjunction with updated third-party security information, detects risks in real-time. It also alerts users at the right time and allows a timely remediation of incidents and breaches.
- Recover: This feature works efficiently for those responsible for identifying incidents and breaches in your Office 365 tenant and for compiling an accurate incident audit. It is capable of fetching historical data for both new as well as existing tenants. It transfers full remediation control over to the users by offering them a single dashboard that has options for disabling user rules, access protocols and authorisation in a few simple clicks. It also offers an option for further fortification to prevent repeat compromise.
A Game Changer for Managed Office 365 Clients: