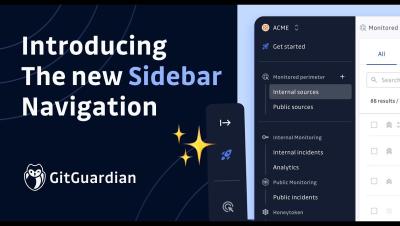
Introducing The New GitGuardian Workspace Sidebar Navigation
We're updating your GitGuardian Workspace user interface, introducing a new sideba experience to make it even easier to navigate and take advantage of our secrets detection platform. We look forward to you using the updated GitGuardian UI to help eliminate secrets sprawl in your organization.