Code injection in Python: examples and prevention
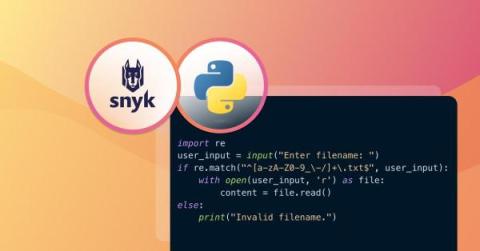
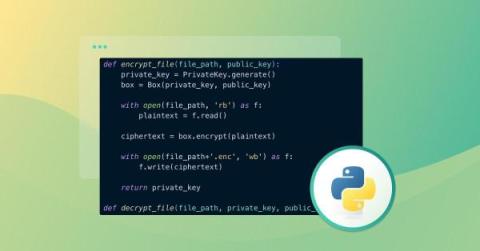
As software becomes increasingly integral to our professional and personal lives, the need to protect information and systems from malicious attacks grows proportionately. One of the critical threats that Python developers must grapple with is the risk of code injection, a sophisticated and often devastating form of cyberattack.