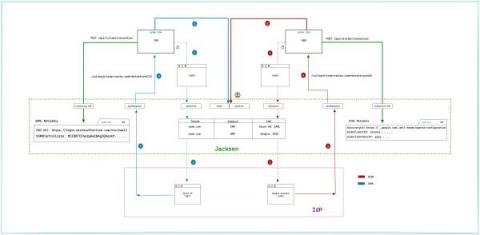
SSO Building blocks - SAML, OAuth 2.0 and OpenID Connect
We have already covered SAML at a high level from both user and application provider points of view. In this post, we'll dive into the technicalities of SAML, OAuth 2.0 and OpenID Connect and how these come together to serve as building blocks for Jackson SSO.