Threat Hunting for macOS - Webinar
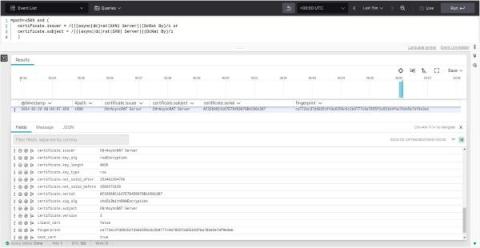
MacOS environments are increasingly becoming targets for sophisticated cyber attacks. This webinar delves into advanced threat hunting techniques within macOS, focusing on the utilization of MUL (macOS Unified Logging) events and comprehensive system telemetry. We look at macOS data sources to uncover hidden threats and enhance detection capabilities.