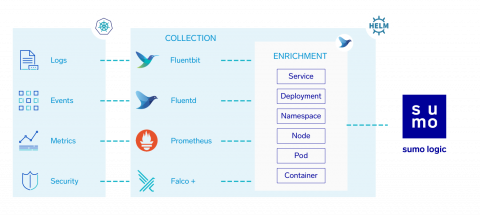
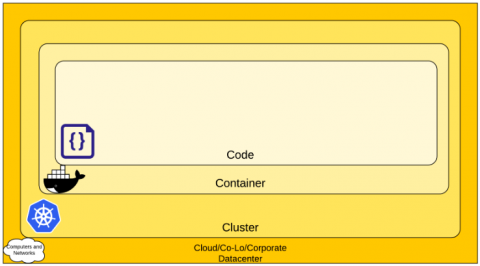
Security monitoring for managed cloud Kubernetes
Photo by chuttersnap on Unsplash Kubernetes (K8s) is an open-source system for automating deployment, scaling, and management of containerized applications. It has recently seen rapid adoption across enterprise environments. Many environments rely on managed Kubernetes services such as Google Kubernetes Engine (GKE) and Amazon Elastic Kubernetes Service (EKS) to take advantage of the benefits of both containerization and the cloud.