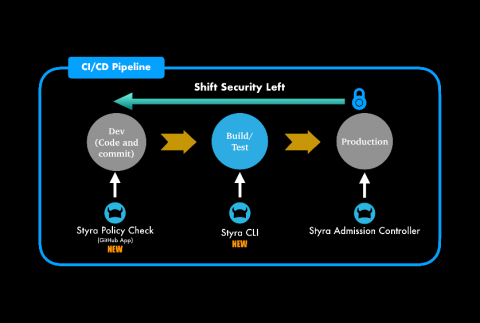
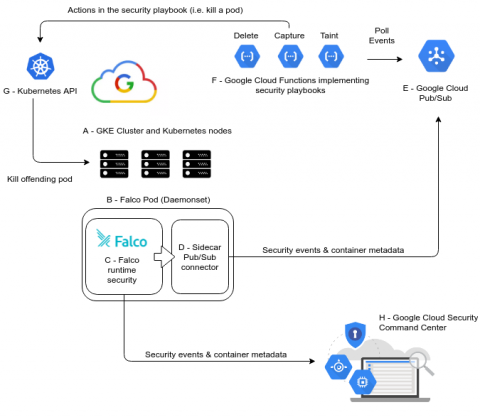
Enhancing Kubernetes Security by Shifting Security Left
In the rapidly evolving world of Kubernetes security & compliance, DevOps and DevSecOps teams are detecting security challenges and compliance issues later in the development & deployment cycles. We are excited to share new features and updates that help DevOps and DevSecOps teams detect issues and ensure compliance throughout the development cycle.