Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Mobile
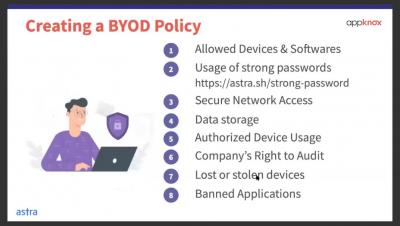
Back Me Up - Hacking Android Apps without Root
We love it when our teams and colleagues are sharing with us their personal projects and findings - this time, Android Apps Penetration Testing by our own Noy Pearl. If you are an android developer, pen-tester, researcher or just like most of us a security enthusiasts - this one is for you.
Working Anywhere With Egnyte: Mobile Guide
In recent weeks, companies and organizations that ordinarily operate in a more “traditional” office environment have had to pivot quickly to flexible and alternative working arrangements. At Egnyte, our goal has always been to help provide safe, secure access to your content no matter where you are, and that goal has become increasingly more important in the current climate.
Android Banking Trojans: History, Types, Modus Operandi
One sunny morning, my breakfast was interrupted by a phone call from a friend who is an entrepreneur engaged in the transportation of various goods. He said that $11,000 disappeared from his bank account during the night. The bank support service could not help. They advised my friend to report this incident to the police. The money transfers were made using the mobile application and confirmed via SMS. Everything looked like completely legal financial transactions.
Why CJIS mobile compliance might be easier than you think
Although we just wrapped up National Cybersecurity Awareness Month in October, security professionals never take a break — because cybercriminals don’t either. That’s especially true for folks who work in law enforcement. Every day they are on the front lines helping to protect the public and solve crimes using Criminal Justice Information (CJI) such as crime reports and fingerprints.
AT&T Cybersecurity Insights Report: Security at the Speed of 5G
While some enterprises appear to be getting an early jump on the security implications of 5G, many are struggling with the implications to the business and the changing security model. This is based on a survey AT&T Cybersecurity conducted with 451 Research of 704 cybersecurity professionals in North America, India, Australia and UK in August - September 2019. Participating organizations spanned 13 industry verticals and each had more than 500 employees.
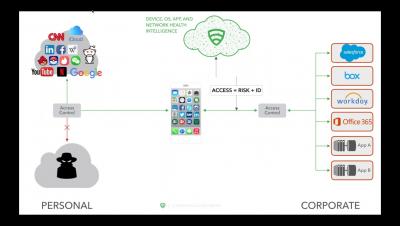
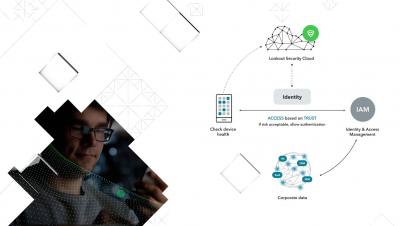
Post-perimeter security 101: Dawn of a borderless world
What You Need to Know About Secure Mobile Messaging in Healthcare
With the majority of people using smartphones these days, texting is all but a given when trying to communicate with your friends or family. But what about your doctor? A recent study determined that 96 percent of physicians use text messaging for coordinating patient care. This can raise eyebrows and red flags.
New Release: ionCube24 App for iOS and Android
We are pleased to announce the release of the ionCube24 app for iOS and Android! With it, you can access ionCube24 wherever you are and monitor your site for performance and security issues. This is a big step forward for ionCube24 giving you ease of access for monitoring your website wherever you are. With notifications and in-app management options you can be aware of issues immediately and act fast. Take a look below to see what the ionCube24 app can do.