Top Challenges in Mobile Application Security Testing (+ Solutions)
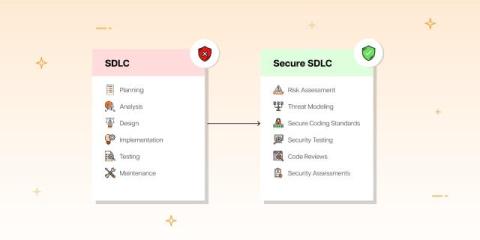
Mobile app security testing identifies and assesses security vulnerabilities in mobile applications, including Android and iOS. It is a part of a more extensive security assessment or penetration test encompassing the client-server architecture and server-side APIs used by the mobile app. Mobile app security testing (MAST) is an afterthought since organizations want to release their apps faster, and development teams are understaffed and overworked. The result?