|
By By Rucha Wele
A dynamic analysis tool for mobile apps is platform and language-agnostic, so you can use the same DAST tools for most applications. As they attack the application externally, they detect configuration issues that other application security testing tools may miss.
|
By By Rucha Wele
Before the introduction of static code analysis tools, securing mobile applications often felt like playing catch-up. Development teams would spend months building features, only to discover critical vulnerabilities late in the release cycle. This last-minute scramble to fix security issues delayed product launches and stretched resources thin—adding more pressure on developers and security teams.
|
By By Subho Halder
Application security has transformed from being an afterthought to a central focus as threats have evolved. What was once about securing code has expanded to protecting the entire application lifecycle. The rise of cloud-native architectures, microservices, and APIs has broadened the attack surface, requiring security teams to rethink their approaches.
|
By By Raghunandan J
Penetration testing tools are necessary for enterprises that want to protect their applications from real-world cyber attacks. These tools identify vulnerabilities that could lead to breaches, like the 2017 Equifax data breach. These specialized tools help identify gaps in software security posture by simulating real-world attacks that vulnerability assessments may not fully expose.
|
By By Harshit Agarwal
Some of the biggest and most successful businesses around the globe adopt a security-first strategy right from day one to ensure sustainability in growth. Regarding scalability, faster time to market, or competitive advantages, security must sit right at the top of business strategy. Security ensures that regular business operations and innovations remain uninterrupted pre or post-production.
|
By Rucha Wele
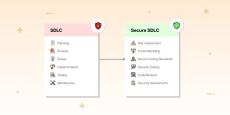
The Software Development Life Cycle (SDLC) provides a systematic framework for developing and maintaining software from conception to modification, producing high-quality software that meets stakeholder and customer requirements within specified time and cost constraints. However, traditional SDLC practices fall short of ensuring thorough application security. Why?
|
By Raghunandan J
With organizations continuing to build and enhance their mobile applications and developers embracing new ways of building applications to improve the speed to market and customer experiences, billions of dollars are invested in Appsec tools. However, 85% of these applications still contain known vulnerabilities, and most breaches occur at the application layer. Automated DAST helps in combating such vulnerabilities.
|
By Subho Halder
Dynamic Application Security Testing (DAST) is an advanced testing method that tests the production environment and analyzes application security at runtime. This type of black box testing identifies real-world vulnerabilities externally without much need for insights into the product provenance of any single component. By simulating real-world attacks in your system, DAST identifies critical security gaps that other vulnerability assessments and static methods might miss.
|
By Subho Halder
This article provides a detailed guide on successfully integrating Swagger UI into web applications using EmberJs as the Javascript framework and Webpack as the module bundler. We will cover the step-by-step process, including any challenges encountered along the way and how we resolved them. For those unfamiliar with Ember Js or Webpack, we have included introductory sections to get you up to speed. If you’re already familiar with it, feel free to skip directly to the integration steps.
|
By Subho Halder
Businesses have gone mobile-first, and with good reason—people are spending more time and more money on their phones than ever before. For instance, in 2023, an estimated 66% or 2/3rds of all online orders were made from mobile devices. And in 2024, businesses are expected to spend $402 billion on mobile advertising. Mobile apps have become the first choice for users for their online activities in banking, e-commerce, media streaming, social media, etc.
|
By Appknox
In the rapidly evolving world of Fintech, trust, and security are of paramount importance. We have gathered an exceptional panel of industry experts who will delve into the challenges faced by Fintech companies in maintaining the trust of their customers and ensuring the security of their banking apps. Join our industry leaders comprising of Subho Halder Majorie Labindao Salinawati Salehuddin Md. Abul Kalam Azad,CISSP,CISA,CISM, CRISC.
|
By Appknox
It's #DataPrivacyWeek. Are you ready to build a secure organization and keep your data safe? Join Appknox's panel discussion with Subho Halder, Raghunath Thiyagarajan, Rajkumar P, and Vijayta Sharma
|
By Appknox
Through this webinar, we aim to help enterprises & individuals understand about cloud security and I-AM policy can play a role to build safe and secure mobile apps that garner trust. It will help you to prevent sensitive data loss and infrastructure exposure, resulting in fraud, reputation damage, and regulatory penalties.
|
By Appknox
About The Webinar: The cybersecurity landscape is constantly evolving, making it a challenge to stay ahead of attackers. They are always looking to exploit & gain access to control sensitive information. This can lead to serious consequences, such as ransomware attacks. This means integrating security as a core part of the development process is becoming even more essential by the day.
|
By Appknox
About The Webinar: Today’s cybersecurity threat landscape is highly challenging. Attackers are constantly on the lookout to exploit security vulnerabilities in applications and systems to gain access to or control sensitive information and launch cyberattacks such as ransomware. With companies spreading sensitive data across different platforms, software as a service (SaaS) platforms, containers, service providers, and even various cloud platforms, it’s essential that they begin to take a more proactive approach to security.
|
By Appknox
Join us in an exciting webinar by Appknox's CISO & Co-Founder, Subho Halder and Vaishali Nagori, Penetration Tester at Appknox on Payment Gateway Related Vulnerabilities. Know how Fortune 500 companies have created superior & secure payment gateways for their customers.
|
By Appknox
Launching a mobile enterprise application is no easy feat and one minor security breach can undo all your hard work in no time. With the right security platform, you can detect and fix security vulnerabilities without losing sleep. Say hello to Appknox, a plug-and-play security solution that secures your mobile enterprise applications in less than 60 minutes. Rated the highest in security products in Gartner and being a high performer on G2crowd for SAST, we set ourselves apart from our competition by allowing you to integrate your SDLC with all project management and CI-CD toolchain.
|
By Appknox
A security-first strategy is a competitive business advantage in today's world. Know how Fortune 500's have created superior and secure digital experiences for their customers.
|
By Appknox
Launching a mobile enterprise application is no easy feat and one minor security breach can undo all your hard work in no time. With the right security platform, you can detect and fix security vulnerabilities without losing sleep. Say hello to Appknox, a plug-and-play security solution that secures your mobile enterprise applications in less than 60 minutes. Rated the highest in security products in Gartner and being a high performer on G2crowd for SAST, we set ourselves apart from our competition by allowing you to integrate your SDLC with all project management and CI-CD toolchain.
|
By Appknox
Unlocking the Secrets of building a secure app Under 60 Minutes Build a culture of Secure Programming in your engineering team . With the amount of (attempted) security breaches and high paced sprint cycles, securing your mobile applications from day 1 is a driving force to ship applications at speed.
|
By Appknox
When you are looking for genuine, inexpensive unbiased information to make your application secure, there is no better source to go to than OWASP. OWASP gives you guidelines to the industry's top threats and security best practices that help ensure your applications are secured. Take a look at this FREE OWASP Guide that covers vulnerabilities from both web and mobile to give you a comprehensive overview of your application's security status.
|
By Appknox
Apple is known to employ slightly more stringent norms as compared to its other counterparts as far as Approving apps is concerned.
|
By Appknox
Detect and eliminate critical threats with the lowest visibility hiding behind the thickest of code. Protect your mobile apps and it's data from malicious attacks.
|
By Appknox
As SaaS businesses continue to evolve in a world of cut throat competition, key decision makers must ensure full accountability of their user's security. Sensitive and personal data should be monitored and kept secure along with innovation and strategic investments. Hence security for SaaS organisations is a critical component as a strategic driver for the growth of business.
|
By Appknox
When we make our way into the ecosystem of security technology and infrastructure initiative, learning about application security trends becomes of utmost importance. The unpredictable COVID-19 situation has made global businesses more vulnerable than ever to cyberattacks and breaches. Be it the Zoom data breach (500k records stolen) or the Marriott (5.2 million records breached), hackers don't seem to miss opportunities to exploit vulnerabilities and gain access to business infrastructures and public records.
|
By Appknox
In public-facing cloud environments with faster than ever deployment and delivery speeds, we need security models that can keep up with the pace. However, security still remains one of the most downplayed affairs in many organizations. While DevOps practices have helped organizations find means to build and react to the market faster, the hurdles of relying on traditional security are still making inroads for more and more threat incidents.
- November 2024 (1)
- October 2024 (4)
- September 2024 (3)
- August 2024 (1)
- July 2024 (4)
- June 2024 (3)
- May 2024 (1)
- April 2024 (2)
- March 2024 (2)
- February 2024 (1)
- January 2024 (5)
- December 2023 (2)
- November 2023 (1)
- October 2023 (1)
- August 2023 (6)
- July 2023 (2)
- June 2023 (6)
- May 2023 (7)
- April 2023 (2)
- March 2023 (7)
- February 2023 (5)
- January 2023 (6)
- December 2022 (2)
- November 2022 (4)
- October 2022 (2)
- September 2022 (3)
- August 2022 (8)
- July 2022 (5)
- June 2022 (10)
- May 2022 (5)
- April 2022 (4)
- March 2022 (2)
- February 2022 (8)
- January 2022 (7)
- December 2021 (6)
- November 2021 (3)
- October 2021 (4)
- September 2021 (3)
- August 2021 (8)
- July 2021 (2)
- June 2021 (8)
- May 2021 (2)
- April 2021 (7)
- March 2021 (7)
- February 2021 (3)
- January 2021 (4)
- December 2020 (3)
- October 2020 (1)
- July 2020 (1)
- April 2020 (5)
- March 2020 (1)
Appknox is the worlds most powerful plug and play security platform which helps Developers, Security Researchers and Enterprises to build a safe and secure mobile ecosystem using a system plus human approach to outsmart smartest hackers.
Our Products:
- Static Application Security Testing (SAST): With 36 different test cases, Appknox SAST can detect almost every vulnerability that’s lurking around by analyzing your source code. Our tests cover security compliances like OWASP Top 10, PCI-DSS, HIPAA and other commonly used security threat parameters.
- Dynamic Application Security Testing (DAST): Detect advanced vulnerabilities while your application is running. Appknox DAST simulates actual attacks on our test environment to analyze, detect and plug those pesky vulnerabilities that can fall prey to runtime and network attacks like MITM.
- Application Programming Interface (API) Testing: Quite different than SAST or DAST, Appknox's APIT tests the server-side of your application. Appknox API scan captures API's at requested endpoints and runs 15+ tests on each of these API's to detect vulnerabilities that may compromise the security of the app servers.
- Manual Application Security Testing (MAST): Nevertheless, the human mind is much sharper than a machine. Hence MAST in our security testing product that utilizes experienced security researchers to test vulnerabilities in your app.
- Remediation for Mobile Apps: Prioritize remediation with a research-driven security evaluation guided by OWASP security standards. Appknox remediation framework is designed to help development teams understand and remediate vulnerabilities without slowing down on SDLC.
Build and deploy world-class mobile apps for your organizations at scale and leave your mobile app security to us.