Understanding API Breaches: Insights from 'Outliers' and the Complexities of Cybersecurity
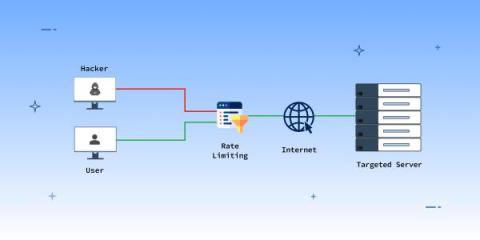
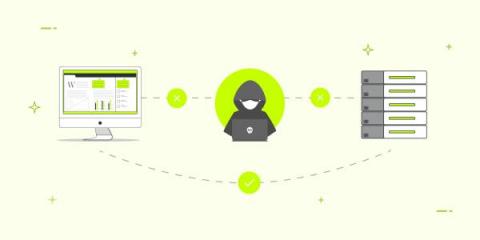
Over the last couple of decades in the cybersecurity industry, I have observed how APIs have gained significant importance in modern cloud-based architectures over the past few decades. In fact, they account for over 80% of all web traffic. However, this increased usage has also made APIs vulnerable to cyber threats. A closer look reveals that APIs are now one of the most prominent threat vectors in the cybersecurity landscape.