Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
January 2022
Interview with a Hacker How are Attackers Targeting Mobile Devices
Critical Requirements for Mobile Security
0:00 Opening
6:06 What is Zero Trust?
11:48 Zero Trust workforce on mobile devices
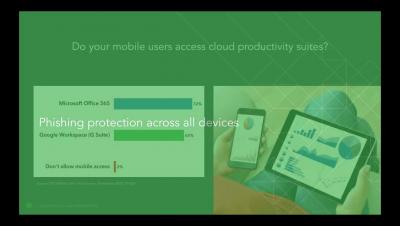
14:57 Enabling Phishing protection on mobile
26:10 Vulnerability management for devices and applications
33:05 Ability to hunt for threats on mobile
43:45 Critical capabilities for comprhensive security
45:20 Q&A
Apps Under Attack - What You Need To Know
0:00 Opening
4:50 What mobile threats are out there?
11:20 Lookout Mobile App solution
13:35 Lookout Threat Discoveries
23:57 Banking Trojans
25:54 Strandhogg
28:40 Detecting Malware
35:36 How does Lookout protect mobile?
Critical Capabilities for Mobile Vulnerability Management
Protecting Mobile Point of Sale and Financial Apps From Cyber Breaches
White Box Cryptography- Everything You Need to Know
In the world of heinous and sophisticated crimes, cryptography is the next-gen solution needed to resolve the concern. Whitebox cryptography combines encryption and obfuscation methods to embed secret keys in application code. The aim is to combine code and key in such a way that an attacker cannot distinguish between the two and the new "white-box" program can be safely executed in an insecure environment.
Microsoft Integration for a secure mobile workforce
Where does mobile fit into security frameworks
Phishing Threats in Mobile-enabled world
Steps to Stay Ahead of Risks and Protect Data Privacy
Technology has advanced our world in countless ways. Every day we bank, shop, conduct business and exchange photos and messages with family and friends online. While digital devices and services offer great convenience, they also pose risks to our data and privacy as the separation between our offline and online lives converges. Data Privacy Week, spanning January 24-28, serves as an important reminder of the importance of protecting our privacy and safeguarding personal information.
Under the Sheets, Practical Android Static Analysis
First off, before we get into the technical details of attacking applications, a few housekeeping bits must be understood. This blog is aimed at technical individuals that already understand at a basic level Android development and architecture, aiming to give security testers and application developers an insight into the ways an attacker may interrogate code to achieve some form of compromise.
How to threat hunt with mobile EDR
Mobile threats are evolving. Is your security?
Modernizing Government Cybersecurity with Zero Trust
Lookout CASB Use Case Demonstration
Get to Know Lookout
How a Large Financial Services Firm Protects Against Data Leakage with Lookout Secure Email Gateway
Regardless of the industry or organization, corporate email is the main cause of unauthorized and accidental data leaks. Employees are constantly sending emails to external parties that may contain sensitive company data, personally identifiable information (PII), trade secrets and other intellectual property.
Pandemic-related cyber threats will persist
Key Criteria for Choosing Mobile App Security Solution Vendor
Mobile phone apps are more popular than ever with a rapidly expanding user base each year. They have literally made everything come to the fingertips of the users and there’s a significant demand for mobile apps for just about everything, generating great competition and pressure among app developers around the world.
Getting the best out of Samsung Knox management with Mobile Device Manager Plus
In case you missed it, Samsung Knox has verified Mobile Device Manager Plus as a Knox Validated Partner solution. This means that our EMM solution meets its business-level requirements for 2022, and that we support a wide range of features to help you get the best out of all your mobile devices that support Samsung Knox capabilities.
Mobile malware will become (even more of) a business
Appknox Research reveals 91% of Fintech Apps Fail Basic Security Tests
The unexpected and rapid switch from the global workforce to the WFH setup caused by the coronavirus pandemic has prompted companies around the world to make extensive infrastructure adjustments to support employees working exclusively from home. According to the new IDC forecast, the number of mobile workers in the US will steadily increase from 78.5 million in 2020 to 93.5 million in 2024 over the next four years.
Introducing next-generation firewall from Palo Alto Networks to support 5G-enabled IoT, OT and IT use cases
Enterprises know they need defenses integrated into each aspect of their network while not being an inhibitor to innovation. Digital transformation realized through new 5G-enabled IoT, Operational Technologies (OT) and IT use cases are no exception. Therefore, security teams need to take a closer look at the best technology to support this innovation.
Best Practices for Mobile App Security Testing for Developers & Non-Developers
Mobile application security testing (MAST) covers a wide range of topics, including authentication, authorization, data security, session management, and vulnerabilities for hacking. The mobile AST market is made up of buyers and sellers of products that identify vulnerabilities and apps used with mobile platforms during or post-development.