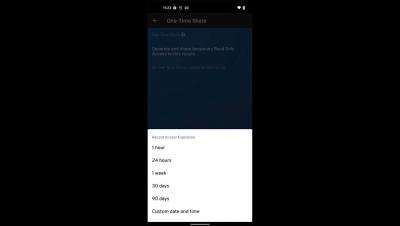
Your Ultimate Social Media Security Checklist [2022 Updated]
Social media is both a boon and a bane. While it has connected billions of people, made them more accessible, and created more possibilities for the end-users. There's no doubt that it has also made them more susceptible to security threats and vulnerabilities. According to We Are Social, there are around 4.62 billion active social media users worldwide. This is precisely the very reason why cyber criminals love social media as well.