Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
November 2021
Achieve Enhanced Cloud Security with DLP
Zero Trust isn't a Buzzword
Achieving Zero Trust? One Size Does Not Fit All
More than a year of near-universal remote work has proven that many of us can reliably stay productive from anywhere — whether it be from home, co-working spaces or otherwise. Businesses have caught wind of this, and according to IDC, 60% of them will continue with remote work or implement a hybrid model even after they reopen their offices again. This calls for a paradigm shift in the way we conduct cybersecurity.
A buyers guide: What to consider when assessing a CASB with Hank Schless
Cloud Applications: A Zero Trust Approach To Security For Healthcare
The Top Business Technology Trends for 2021-2022
With the new year just around the corner, the world of business is set to see great change. From 5G and the Internet of Things to the blockchain, new technology trends are creating a digital transformation for companies on a global level. In this article, we’ll take a look at the latest trends in technology to keep an eye out for in 2022 and beyond.
2022 Cybersecurity predictions
In 2020, we saw cybersecurity move from a technical problem to become a business enabler. In 2022, we will see 5G go from new technology to a business enabler bringing previously unimaginable use cases because of its high bandwidth and lower latency. Data from the current AT&T Cybersecurity Insights Report shows that 5G technology is being driven by the line of business and has been siloed between IT and OT organizations.
Lookout CASB Named a Major Player in 2021 IDC MarketScape Cloud Security Gateways
I am excited to share a major milestone for our company: the Lookout Cloud Access Security Broker (CASB) has been named a Major Player in the 2021 IDC MarketScape Worldwide Cloud Security Gateways (CSG) Vendor Assessment (Doc # US48334521, November 2021). When Lookout acquired CipherCloud back in March 2021, the two companies came together with a mission to build a platform that provides intelligent Zero Trust access by leveraging in-depth telemetry from endpoint to cloud.
Mobile Phishing: A massive threat on a small screen
Our SASE Journey: Lookout Head of IT Talks Shop
Like other organizations that are adopting a permanent hybrid or remote-first work environment, Lookout is using our Secure Access Services Edge (SASE) platform to implement cybersecurity that is not tied to the physical office spaces where employees used to work. SASE is a security framework defined by Gartner that has been adopted by many organizations to enable intelligent Zero-Trust access from anywhere without hindering productivity.
The growing threat of mobile phishing
Lookout - Phishing & Content Protection
What is OWASP Mobile Security Testing Guide (MSTG)?
With millions of apps being released every day and ever-changing feature additions, it is more important than ever for enterprises to focus on security to prevent data breaches. According to Checkpoint, in 2020, 97 per cent of enterprises were confronted with mobile threats employing a variety of attack vectors. What is Mobile Security Testing Guide (MSTG)? The MSTG is a comprehensive manual for mobile app security testing.
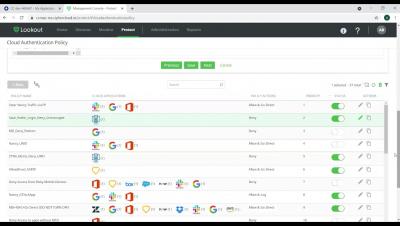
Lookout ZTNA - Setting up an access policy for unmanaged devices
Lookout CASB - Preventing Sensitive Data Leakage to Personal Channels in Slack
Lookout CASB - Secure Collaboration and Compliant Sharing of Content in Slack
Lookout CASB provides enhanced visibility into activities in Slack
Lookout CASB Protects Sensitive Data in Slack by Masking data and Watermarking
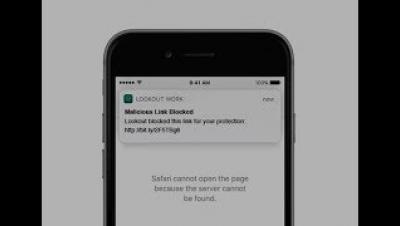
Lookout Protects Against Mobile Phishing Threats
Zero Trust? Don't Forget Your Mobile Fleet
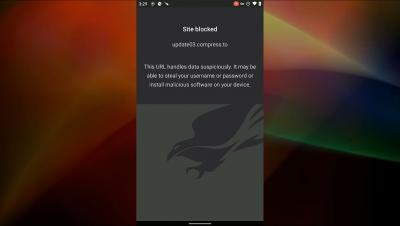
Protecting Users from Malicious Sites with Falcon for Mobile
Lookout Data Shows Already Strained Energy Industry Faced With 161% Surge in Mobile Phishing
A few months ago, the largest U.S. pipeline operator, Colonial Pipeline, was forced to halt operations for nearly a week due to a ransomware attack. While it ultimately didn’t stop consumers from buying gasoline, the incident forced the company to pay $4.4 million in ransom payment and illustrated just how vulnerable energy organizations are to cyberattacks.