|
By Sai Kit Chu
Want to block distracting websites, monitor internet use, and keep your network secure against web-based threats? This list of the best internet filtering software covers website blocking solutions that are suitable for businesses, parental control, Mac users, and more.
|
By Dale Strickland
See how CurrentWare ensures student safety in our web filtering software for schools case study Safeguarding sensitive information is crucial for educational institutions and libraries. The FCC’s Schools and Libraries Cybersecurity Pilot Program aims to bolster the cybersecurity infrastructure of these institutions by providing essential funding for robust security solutions.
|
By Dale Strickland
Cybersecurity Maturity Model Certification (CMMC) is a critical framework for protecting sensitive information within the defense industrial base (DIB). With the transition to CMMC 2.0, organizations that do business with the Department of Defense (DoD) must ensure they meet evolving cybersecurity standards.
|
By Dale Strickland
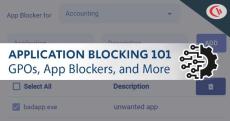
In today’s digital landscape, safeguarding your organization’s network from unauthorized applications is paramount. One effective strategy is blocking executable (.exe) files using application blocking software or an Active Directory Group Policy. This tutorial will provide step-by-step guides that will teach you how to block executable files in Windows using various methods.
|
By Dale Strickland
In today’s digital world, cyber threats are a constant concern for businesses of all sizes. According to a 2024 survey by the UK government’s Department for Science, Innovation & Technology (DSIT), 74% of large and 70% of medium businesses reported experiencing a recent cyber attack. Data breaches, malware attacks, and phishing scams can cripple operations and damage your reputation.
|
By Guest Contributor
Businesses of all shapes and sizes can fall victim to data breaches. Unfortunately, even with the best privacy and security measures in place, hackers are continually becoming more skilled at beating them. A well designed and implemented data breach response plan is essential if businesses are to minimize the effect of data breaches and protect their reputation. Not only that, but they can reduce the financial damage to the business and better position the organization for recovery.
|
By Dale Strickland
In our increasingly digital world, USB drives remain a convenient way to transport and store data. However, the use of these devices in corporate networks introduces several security concerns. This blog post will cover USB security best practices to equip you with the knowledge to safeguard your company’s valuable information against the security risks of removable media devices such as flash drives.
|
By Dale Strickland
To help you keep legacy systems protected against the dangers of USB devices, CurrentWare now offers a dedicated version of its USB blocker AccessPatrol for Windows XP, allowing you to easily monitor and block USB ports on Windows XP. With AccessPatrol USB port blocker for Windows XP you can create an “allowed list” of authorized USB devices, grant different access levels (read-only, full access, or no access), and get insights into file transfers to portable storage devices.
|
By Dale Strickland
Employee theft isn’t just a financial issue; it can erode trust and damage company morale. These employee theft statistics highlight the prevalence of workplace theft across key categories including data theft, time theft, fraud and embezzlement, insider threats, and retail theft.
|
By Guest Contributor
Navigating the line between workplace privacy restrictions and employee rights is getting more complicated as employees shift to hybrid and remote settings. According to Code42’s 2023 Data Exposure Report, data loss caused by business insiders costs companies an average of $16 million per incident. Moreover, 81% of companies believe that hybrid work is one of the main reasons data security training is necessary.
|
By CurrentWare
Don’t let internet abuse run rampant in your organization. Take back control over web browsing with a free trial of BrowseControl. BrowseControl is an easy-to-use web content filtering software that helps organizations enforce policies, improve productivity, reduce bandwidth consumption, and meet compliance requirements - no matter where their users are located.
|
By CurrentWare
Don’t let a preventable data leak ruin your organization. Take back control over portable storage devices with a free trial of AccessPatrol USB device control software.
|
By CurrentWare
CurrentWare version 9.0 is here! This update introduces transparent packet filtering technology, allowing for significant enhancements to the tracking and restriction capabilities of the CurrentWare Suite. By upgrading to CurrentWare v9.0 you will have greater protection against the data security risks of cloud storage services, potentially malicious file downloads, network share drives, and more!
|
By CurrentWare
Don’t let a preventable data leak ruin your organization. Take back control over portable storage devices with a free trial of AccessPatrol USB device control software.
|
By CurrentWare
This is a live recording of the CurrentWare version 7.0.1 webinar that took place on June 08, 2022.
|
By CurrentWare
“CurrentWare saved us a lot of time and money; when the employee was questioned about the data transfer they folded. I cannot thank all of you enough for this software. Being able to audit removable drives is invaluable.” A lot has changed in the world since our first case study interview in 2021 with Vincent (Vinny) Pecoreno, the Network Administrator for Viking Yachts.
How to Enable Two-Factor Authentication (2FA) in the CurrentWare Suite | CurrentWare v7.0.1 Tutorial
|
By CurrentWare
This video will teach you how to set up two-factor authentication (2FA) in CurrentWare version 7.0.1. Two-factor authentication provides an extra layer of security if anyone other than you attempts to log in to your CurrentWare web console using your account.
How to Migrate Your Legacy CurrentWare Software to the New Web Console (2022 Tutorial) | CurrentWare
|
By CurrentWare
In this video you will learn how to easily upgrade from the legacy desktop version of the CurrentWare Suite to the new web console. By upgrading to the web console you'll gain access to a variety of new capabilities.
|
By CurrentWare
This is a live recording of the CurrentWare version 7.0 webinar that took place on March 10, 2022.
CurrentWare Overview - Employee Monitoring, Web Filtering, Device Control, & Remote PC Power Manager
|
By CurrentWare
In this video, we provide an overview of the features available in the CurrentWare suite.
- January 2025 (1)
- September 2024 (2)
- July 2024 (1)
- June 2024 (3)
- May 2024 (1)
- April 2024 (1)
- March 2024 (1)
- February 2024 (1)
- January 2024 (1)
- October 2023 (1)
- September 2023 (1)
- August 2023 (2)
- June 2023 (1)
- May 2023 (1)
- April 2023 (1)
- March 2023 (1)
- July 2022 (2)
- June 2022 (4)
- May 2022 (3)
- April 2022 (1)
- March 2022 (4)
- February 2022 (3)
- January 2022 (2)
- December 2021 (3)
- November 2021 (3)
- October 2021 (2)
- September 2021 (1)
- August 2021 (1)
- July 2021 (2)
- May 2021 (3)
- April 2021 (2)
- February 2021 (1)
- December 2020 (4)
- November 2020 (1)
- October 2020 (2)
CurrentWare’s user activity monitoring, web filtering, and device control software gives you advanced control and visibility over your entire workforce.
Improve employee productivity, data security, and business intelligence with advanced awareness and control over how technology is used in your organization. Each solution operates from the same central console, allowing you to easily manage the entire CurrentWare Suite from the convenience of a web browser.
Discover Our Products:
- Employee Monitoring: BrowseReporter is a versatile employee monitoring software to track productivity and efficiency. Easily monitor web browsing and application usage with intuitive user activity reports.
- Web Filtering: BrowseControl is an easy-to-use website blocking software for restricting internet access. Enforce internet use policies, block distracting websites, and improve internet security with granular internet access control policies.
- Device Control: AccessPatrol is a data loss prevention and USB control software to protect sensitive data against theft to portable storage devices. Block USB devices and other peripherals to mitigate the threat of USB malware and data leakage.
- PC Power Manager: enPowerManager is an effective solution for remotely managing PC power policies across an enterprise to conserve energy and reduce costs. With a simple click of the mouse computers can be remotely shutdown or booted automatically at different times during the day.
Intuitive and Flexible Solutions.