Dark Crystal RAT Agent Deep Dive
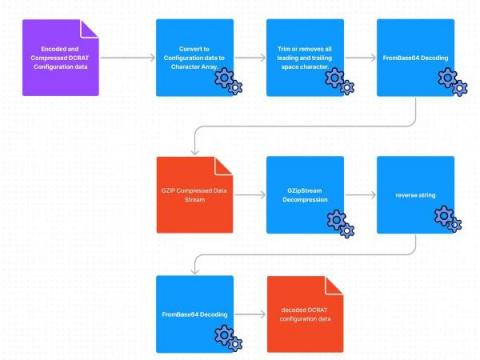
The Splunk Threat Research Team (STRT) analyzed and developed Splunk analytics for this RAT to help defenders identify signs of compromise within their networks. Remote Access Trojans (RATs) are one of the most common tools used by threat actors as a malicious payload to attack targeted hosts and steal information. One example is the Dark Crystal RAT (DCRat) that is capable of remote access, post exploitation and data exfiltration.