Privileged Access Management Best Practices Using SSH and Teleport
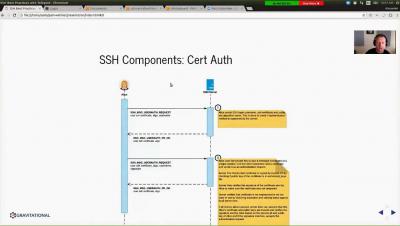
Gravitational CTO, Sasha Klizhentas, goes through the best practices for setting up privileged access management when using SSH to access cloud-native server infrastructure. He also describes how these concepts are applied to Teleport - privileged access management for elastic infrastructure that doesn't get in the way.