Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Outpost24 Public GitHub Now Available
Hello, World! For the first time, Outpost24 is releasing public repositories in GitHub!
SOC 2 Certification - Table Stakes for B2B SaaS
Just like how computers use trusted third parties and chains of trust to connect with one another, organizations use (admittedly much slower and more human powered) authoritative standards organizations (AICPA) and certified audit firms to create a trust system between organizations.
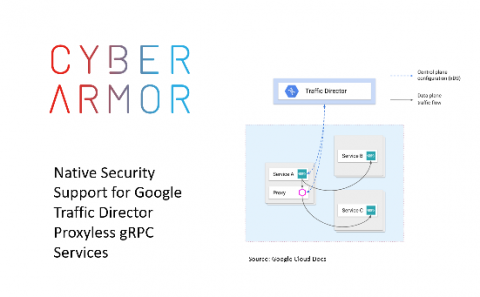
Cyber Armor for Google Traffic Director gRPC Proxyless Services
In its latest announcement of Traffic Director’s support for gRPC Proxyless services in service mesh Google addresses the well-known (yet less spoken of) trade offs for using sidecars to handle networking on behalf of your applications.
Securing Your Kubernetes Journey with ChartCenter
Adopting cloud native technologies like Kubernetes and Helm means your company’s operations can sail swiftly across the globe’s oceans to reach teams and customers. But there are dangers in the deep. With many components in Kubernetes, securing every dimension can be quite challenging and require a bit of learning curve. Let’s identify some important best practices that can help you to steer straight.
Unified cloud-native authorization: Policy everywhere and for everyone
When we started Styra, we set out to rethink authorization and policy for the cloud-native environment. We knew that new risks and challenges would emerge as companies embraced the cloud and began using a whole new host of technologies and architectures for building applications. The constant changes and dynamic runtime of the cloud-native environment complicated matters even more.
Leonid Sandler, Founder and CTO, on the Inspiration behind Cyber Armor
Leonid Sandler, Co-Founder and CTO of Cyber Armor, set for an interview with Safety Detective’s Aviva Zacks on the inspiration behind the company.
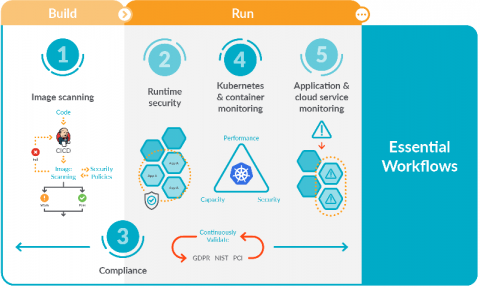
5 Essential workflows for secure DevOps
Focusing on these five essential workflows for secure DevOps will help you get started implementing monitoring, security, and compliance for containers and Kubernetes. You might be starting to adopt DevOps and find that it dramatically simplifies deploying applications in containers and Kubernetes. However, you probably also found that it adds a new set of complexities for managing, securing, and troubleshooting applications.
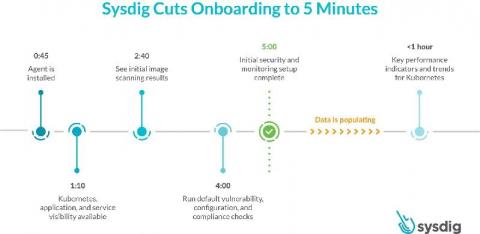
Sysdig cuts onboarding for container and Kubernetes visibility and security to 5 minutes
Today, we are excited to announce a faster onboarding for Kubernetes visibility and security. With the SaaS-first approach and new enhancements to the Sysdig Secure DevOps Platform, you can get results after just a five-minute setup. This release includes a new guided onboarding process, out-of-the-box dashboards as part of curated essential workflows, and a new Sysdig Essentials tier. 5 minutes to onboard secure DevOps - YouTube An error occurred.