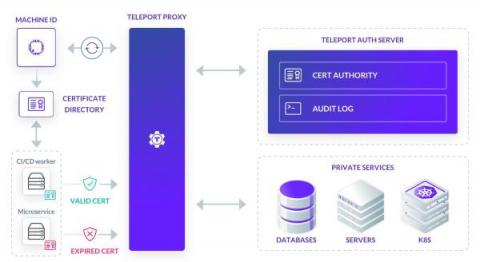
How We Built Machine ID
The DevOps workflow is all about automation driven by machine-to-machine access. To maintain the automated DevOps pipeline, engineers configure service accounts with credentials such as passwords, API tokens, certificates, etc. The issue is that engineers often fall into the security mispractice of creating long-lived credentials for service accounts to facilitate automation and lessen manual intervention.