Detect infrastructure drift and unmanaged resources with Snyk IaC
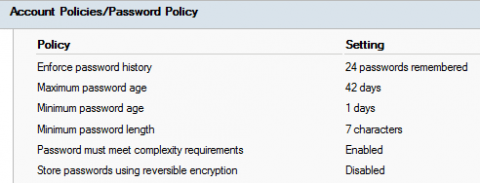
As a developer, you’re probably using some infrastructure cloud provider. And chances are, you automate parts of your infrastructure using infrastructure as code (IaC), so deployments are repeatable, consistent, easily deployable, and overall, more secure because code makes parameters more visible.