Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
How to Generate and Configure SSH Certificate-Based Authentication
The SSH protocol offers multiple authentication options: passwords, public keys and certificates. Certificate-based authentication is the most secure of them all, but historically, it has been the most complicated to set up. This tutorial guides you through simple steps to configure certificate-based authentication for an OpenSSH server. First, let's consider the differences between certificates and keys. As you can see, an SSH key is a binary proposition.
FROGBOT : Securing your git repository!
Why you need a Kubernetes admission controller
Unless you have experience as a Kubernetes operator or administrator, admission controllers may be a new feature for you. These controllers work mostly in the background and many are available as compiled-in plugins, but they can powerfully contribute to a deployment’s security. Admission controllers intercept API requests before they pass to the API server and can prohibit or modify them.
What is Policy Based Access Management?
We’re excited to be included in the first Policy Based Access Management (PBAM) market report! The KuppingerCole Analysts AG’s 2022 Market Compass provides an excellent overview of how the access market is transforming and emerging vendors in the space.
Generating fake security data with Python and faker-security
Snyk recently open sourced our faker-security Python package to help anyone working with security data. In this blog post, we’ll briefly go over what this Python package is and how to use it. But first, we’ll get some context for how the factory_boy Python package can be used in combination with faker-security to improve your test-writing experience during development. Note: Some knowledge of Python is helpful for getting the most out of this post.
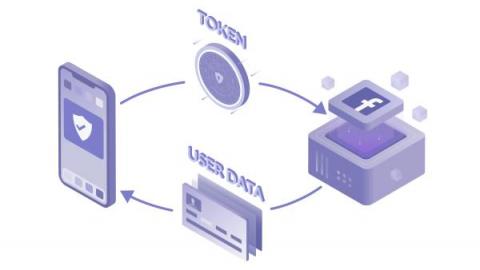
How OAuth 2.0 Works
The modern human likely has profiles on dozens of applications. Whether it’s social media applications, music/video streaming, or workspace resources, each of us must manage accounts that contain personal information. Over time, these siloed applications have become increasingly connected. Twitter allows news sites to directly tweet, Discord searches Facebook for suggested friends, and Jira creates user accounts using Github profiles.
Cybernews/ WhiteSource: It's No Longer a Matter of 'If', but 'When' an Organization Will Be Targeted by Threat Actors
From ransomware and viruses to data breaches, there are many types of security threats to look out for. Because they’re becoming more complex, it’s getting more difficult to secure your organization and avoid the financial and reputational consequences. While some organizations use traditional security measures, such as encrypting data or using antivirus software, businesses should also take a look at more advanced solutions, such as open source security and license management services.
How Software Workflow Integration Drives Product Security
Shift left approaches to software development can lead to enhanced software security without creating more work for developers. These initiatives are made possible in large part by workflow integration. Workflow is a big part of software development, because when it’s automated, workflow is what enables teams to complete tasks more quickly and increase efficiency and accuracy.