Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Cyberattacks
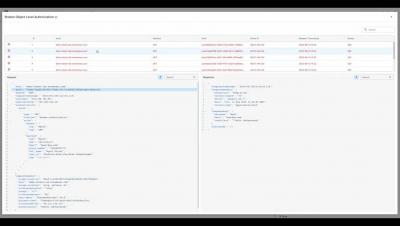
What You Need to Know About the 3CX Supply Chain Attack
Supply Chain Attack Targeting 3CX Softphone Application
Coffee Talk with SURGe: The Interview Series featuring Allan Liska
The Tri Counties Bank in Chico Gets Hacked by a Cyber Gang
Banks are entrusted with a great deal of personal information, money, and more by their customers. When a bank isn't able to secure those things, it's a major issue. This is an issue that the Tri-Counties Bank in Chico faced earlier this year. It wasn't money that the bank failed to protect, but customer information. The bank suffered from a serious cyber attack and lost confidential information in the process.
CrowdStrike Falcon Platform Detects and Prevents Active Intrusion Campaign Targeting 3CXDesktopApp Customers
We will continue to update on this dynamic situation as more details become available. CrowdStrike’s Intelligence team is in contact with 3CX. On March 29, 2023, CrowdStrike observed unexpected malicious activity emanating from a legitimate, signed binary, 3CXDesktopApp — a softphone application from 3CX. The malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a small number of cases, hands-on-keyboard activity.
Killnet and AnonymousSudan DDoS attack Australian university websites, and threaten more attacks - here's what to do about it
Over the past 24 hours, Cloudflare has observed HTTP DDoS attacks targeting university websites in Australia. Universities were the first of several groups publicly targeted by the pro-Russian hacker group Killnet and their affiliate AnonymousSudan, as revealed in a recent Telegram post. The threat actors called for additional attacks against 8 universities, 10 airports, and 8 hospital websites in Australia beginning on Tuesday, March 28.
Runtime Protection Demo - Stop attacks in real-time
New Vendor Email Compromise Attack Seeks $36 Million
The details in this thwarted VEC attack demonstrate how the use of just a few key details can both establish credibility and indicate the entire thing is a scam. It’s not every day you hear about a purely social engineering-based scam taking place that is looking to run away with tens of millions of dollars. But, according to security researchers at Abnormal Security, cybercriminals are becoming brazen and are taking their shots at very large prizes.