Cloud Threats Memo: Misconfigurations as a Threat Vector Continue to Rise
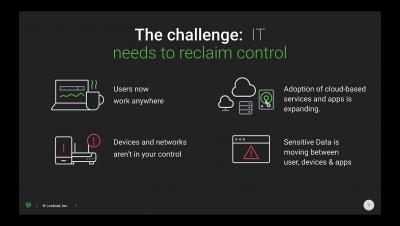
In this hyperconnected world, where 70% of users continue to work remotely, sharing data in real-time with partners and customers leveraging the flexibility of the cloud is a fundamental aspect for the daily operations of businesses worldwide. In this scenario, the risk of misconfigurations exposing sensitive data continues to be a serious (and frequent) concern.