8 Best Practices for Data Security in Hybrid Environments
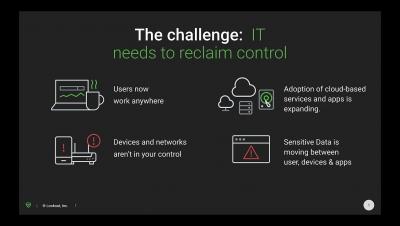
Operating in hybrid environments can get really tricky at times. As more and more organizations are moving their sensitive data to the public cloud, the need to keep this data secure and private has increased significantly over time. While handling their valuable datasets within their respective environments, companies need to ensure utmost data security and compliance to meet the regulations set by various governments.