Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
Multiple Junos OS Vulnerabilities Could lead to Unauthenticated Remote Code Execution
How we found a prototype pollution in protobufjs - CVE-2023-36665
9 Steps to Protect Against the Next MOVEit/MFT Attack
By now, the facts of the recent MOVEit breach are well known (although the victim total keeps climbing), but it never hurts to be reminded that these attacks do not take place in a vacuum and threat actors are more than happy to repeatedly use the same tactics if their targets remain vulnerable. Trustwave SpiderLabs, has tracked and documented these events explaining how threat actors were found to be exploiting three vulnerabilities, including a zero-day, (CVE-2023-34362, CVE-2023-35036.
Introducing Snyk's new Risk Score for risk-based prioritization
We’re happy to announce the open beta availability of Snyk’s new Risk Score! Replacing the existing Priority Score, the new Risk Score was designed to help you prioritize more effectively by providing you with an accurate and holistic understanding of the risk posed by a given security issue.
Uncover API Vulnerabilities with Posture Management
Vulnerability Management - What you need to know
Vulnerability management (VM) is the process of detecting, prioritizing, remediating, and auditing security vulnerabilities in systems and software. This critical process minimizes the organization’s “attack surface” by installing the most current software updates and properly hardening computer configuration.
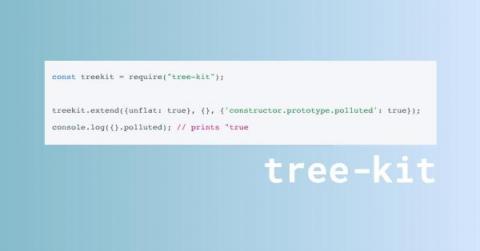
New Vulnerability in tree-kit: Prototype Pollution - CVE-2023-38894
How to Respond to Ivanti EPMM/MobileIron Vulnerabilities (CVE-2023-35078)
Can machines dream of secure code? From AI hallucinations to software vulnerabilities
As GenerativeAI expands its reach, the impact of software development is not left behind. Generative models — particularly Language Models (LMs), such as GPT-3, and those falling under the umbrella of Large Language Models (LLMs) — are increasingly adept at creating human-like text. This includes writing code.