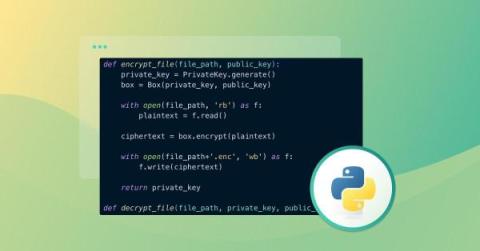
File encryption in Python: An in-depth exploration of symmetric and asymmetric techniques
In our modern world, we constantly share private, confidential, and sensitive information over digital channels. A fundamental component of this communication is file encryption — transforming data into an unreadable format using encryption algorithms.