Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Cloud Threats Memo: Protecting Against Hancitor Distributed Through Malicious Office Documents
Hancitor (AKA CHanitor, Tordal) is a popular macro-based malware distributed via malicious Office documents delivered through malspam. In the latest campaigns, particularly active between October and December 2020, the malware has been distributed via DocuSign-themed emails asking the victims to review and sign a document. The fake DocuSign link downloads a Microsoft Word document whose malicious macro, once enabled, installs the Hancitor malware.
In Search For a Perfect Access Control System
Every cloud has its own identity and access management system. AWS and Google use a bunch of JSON files specifying various rules. Open source projects like Kubernetes support three concurrent access control models - attribute-based, role-based and a webhook access control, all expressed using YAML. Some teams are going as far as inventing their own programming language to solve this evergreen problem.
Intuit: Dev-First Cloud Native Application Security
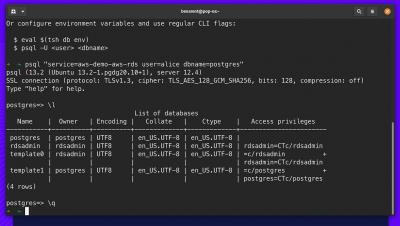
Using Teleport to Audit Postgres and MySQL Database Access
0:00 Introduction
0:26 Deployment Overview
1:31 Why use Teleport?
2:05 tsh setup
3:37 psql demo
4:25 Teleport Audit log
5:21 fleund Overview
6:01 Kibana Demo
6:35 Learn more at https://goteleport.com/database-access/
#postgres #mysql #teleport
Key Differences Between a Public and a Private Cloud
Cloud security. Cloud architecture. Cloud storage. As you start scaling your business, you know “the cloud” is an important element of your IT capabilities. But, it can be a little confusing to understand the ins and outs of “the cloud” — especially when it comes to using cloud-based tools for your company to work remotely. Before we get into private vs public clouds, let’s quickly establish what we mean by cloud computing.
The Role of AI and ML in Preventing Cybercrime
According to a seminal Clark School study, a hacker attacks a computer with internet access every 39 seconds. What’s more, almost a third of all Americans have been harmed by a hacker at one point or another, and more than two-thirds of companies have been victims of web-based attacks. A 2020 IBM study showed that the total cost of data breaches worldwide amounted to $3.9 million, which just may sound the death knell for many businesses affected by breaches.
Cloud-Based Storage Misconfigurations - Understanding the Security Risks and Responses
Misconfigurations remain one of the most common risks in the technology world. Simply telling organisations to “fix” this problem, however, is not as easy as it might first seem because there’s a myriad of technologies at play in modern infrastructure deployments. All of this results in a complicated mix of hardening approaches for each system. What is key, then, is to identify where hardening is required and then consider the methodology for each area.
SolarWinds Orion Security Breach: A Shift In The Software Supply Chain Paradigm
The recent SolarWinds breach highlights a new paradigm in the Software Supply Chain. When compared simply to the code itself without any additional tools, Proprietary Code is no more secure than Open Source. By contrast, many would argue that Open Source Code is more secure due to a faster fix/patch/update cycle and the pervasive access to source code (Clarke, Dorwin, and Nash, n.d.).