Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Is Your Company's Website Compromising Customer Data?
If you are a security, compliance, and privacy professional, it’s time to focus on an often-ignored issue—client-side security. While many organizations dedicate significant resources to protecting their servers, there’s a critical question to consider: are you also safeguarding what’s happening on your users’ browsers?
Understanding the Role of a Partition Lawyer in Real Estate Cases
Are you facing a real estate dispute over property ownership or division? Navigating real estate disputes can be challenging. This is especially true when co-owned properties are involved. If you're in such a situation, understanding the role of a partition lawyer is essential. These legal professionals are well-equipped to handle partition actions. In this article, we will look at how a partition lawyer helps with partition case resolution. Read on to ensure a fair division of co-owned property and protect legal rights.
Mastering Ransomware Defense For Small Businesses
Ransomware poses a significant threat to small businesses by locking critical data and demanding hefty ransoms. Understanding the mechanisms and vulnerabilities exploited by cybercriminals is crucial in safeguarding your operations. This guide will walk you through practical steps to fortify your defenses, detect threats early and ensure swift recovery.
What is a C3PAO? Accreditation, Process, Audits & More
Cybersecurity is a complex business, and there are numerous standards and frameworks meant to help businesses achieve some level of security and protection in a hostile world. Among those programs is CMMC, the Cybersecurity Maturity Model Certification. With a new final rule in the finishing stages, it’s critical to know the details if it’s important to your business. CMMC is an initiative and a framework developed and maintained by the United States Department of Defense.
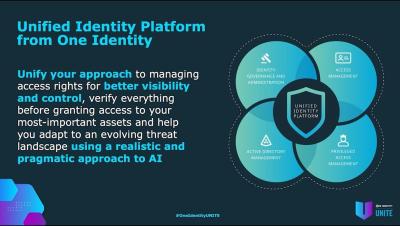
CEO keynote - The market is screaming for consolidation
Listen to Mark Logan, CEO of One Identity on the future of the identity fabric.
A Year of Recognition: Trustwave's 2024 Industry Analyst Highlights
As we reflect on the past year, we're incredibly proud to share that Trustwave has been recognized by some of the most respected industry analyst firms. These accolades, spanning a variety of security services and global regions, solidify our position as a global leader in cybersecurity.
SASE in China: Secure, Reliable Connectivity
China is a vital market for global enterprises but often poses connectivity challenges due to strict regulations, unpredictable network performance, and complex compliance requirements. But what if you could turn these challenges into opportunities? Join Philip Walley as he introduces Cato SASE, the ultimate solution for seamless, secure, and high-performance global connectivity to and from China.