Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Demo
The Forescout Platform
Manage risks. Contain events. Mitigate threats. The Forescout Platform continuously identifies, protects and ensures the compliance of all managed and unmanaged cyber assets – IT, IoT, IoMT and OT – without business disruption. It delivers comprehensive capabilities for network security, risk and exposure management, and extended detection and response. With seamless context sharing and workflow orchestration via ecosystem partners, it enables you to more effectively manage cyber risk and mitigate threats.
What is Business Logic? | Noname Security
Business logic refers to the set of rules that govern the behavior of a business. At its core, business logic is used in making decisions based on what makes sense for your company. Despite these benefits, business logic doesn’t come without risk as vulnerabilities if your applications rely on business logic to function.
What is Data Exfiltration? | Noname Security
Data exfiltration is the unauthorized transferring of data out of a secure environment, usually for malicious purposes. It’s improper exporting of data; a data breach that ends up with data in the wrong hands. One might say it’s a fancy word for stealing. Outsiders, employees, and contractors can exfiltrate data, but it is often difficult to detect until it’s too late.
Unlocking the Future: Brivo's Revolutionary Access Solutions for Every Space
Dive into the world of unparalleled security and convenience with Brivo's cutting-edge access control solutions. Whether it's a commercial estate, a cozy residential space, or a sprawling enterprise, Brivo has the technology to secure every corner. 🔑🌐 In this video, we explore how Brivo's innovative approach is transforming the way we think about access control and smart spaces. From seamless integration to user-friendly interfaces, discover how Brivo serves any facility with ease and efficiency. 🌟
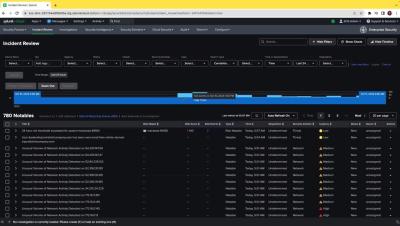
SIEM in Seconds - Splunk Enterprise Security Auto Refresh and Timeline of Notable Events
SOC analysts are overwhelmed sifting through a sea of notable events. They are unable to prioritize events and act fast. With Auto Refresh in the Incident Review interface, users will not have to re-run the Incident Response search or refresh the page. Furthermore, an interactive timeline for notable events within the Incident Response interface enables the SOC to quickly prioritize critical incidents.
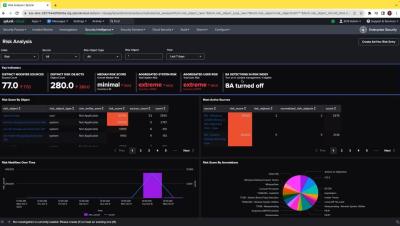
SIEM in Seconds - Splunk Enterprise Security Enhanced Risk Analysis Dashboard
With the enhanced risk analysis dashboard in Splunk Enterprise Security, security analysts can now monitor user entity risk events from detections across risk-based alerting and behavioral analytics, which provides a deeper, and more holistic, layer of visibility across all detection events.
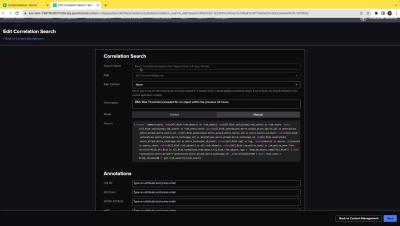
SIEM in Seconds - Streamline Investigations with Splunk Enterprise Security
A SOC analyst's day-to-day tasks involve investigating notable events to gather information about security incidents. Recent enhancements within the Incident Review and Risk Analysis dashboards in Splunk Enterprise Security allows analysts to streamline their investigation process and reduce the number of manual tasks they perform daily. Multiple drill-down searches on correlation rules, updates to "dispositions" in the Incident Review dashboard, and hyperlinks in Correlation Search “Next Steps” allow for faster, more efficient investigations.