Identifying and Avoiding Malicious Packages
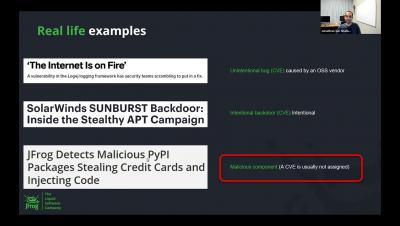
Securing your software supply chain is absolutely critical as attackers are getting more sophisticated in their ability to infect software at all stages of the development lifecycle. This webinar will be a technical showcase of the different types of malicious packages that are prevalent today in the PyPI (Python) and npm (Node.js) package repositories. All examples shown in the webinar will be based on real data and malicious packages that were identified and disclosed by the JFrog security research team.