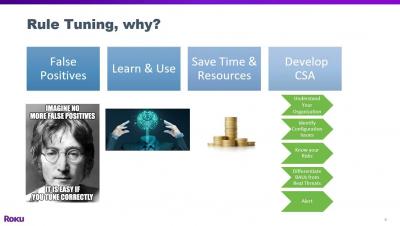
SIEM rule tuning to develop cyber situational awareness
Every organization runs at different levels of acceptable risk. When a SIEM rule generates an alert one company might deem it a critical risk while another will shrug it off as business as usual. Knowing how your organization runs and understanding your security posture can bring you improved cyber situational awareness.