Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Public Sector
Tanium XEM and ROI: A Powerful Duo for Government Cybersecurity
How Forrester Consulting's insights helped Tanium develop an analysis tool that can shed light into the economic impact of XEM for state and local government.
The Top 7 Cyberattacks on U.S. Government
In a world where ones and zeros are the new battleground, these threats, cyberattacks have become a significant threat to governments worldwide. The United States, with its vast array of government agencies and critical infrastructure, is no exception. Cybersecurity threats that impact the public sector range from state-sponsored attacks to financially motivated hacking groups. In this blog post, we’ll delve into the top 7 cyberattacks on the U.S.
7 tech challenges that can be collaboration opportunities for global governments
Safeguarding K-12 Education: A Whole-of-State Approach to Cybersecurity for Chromebook-Centric School Districts
In today’s rapidly evolving digital landscape, K-12 school districts are harnessing the power of technology to transform education. The widespread adoption of Chromebooks has revolutionized the learning process, providing students with tools for collaboration, research and creativity. However, along with these advancements come unprecedented cybersecurity challenges that demand a comprehensive strategy.
Becoming FedRAMP and StateRAMP Authorized, Part 2 - Common FedRAMP Mistakes You Can Avoid
August 31, 2023 By Isac Hur, Senior FedRAMP/ StateRAMP/ CMMC Practice Lead and Quality Assurance As a compliance auditor and practitioner in the FedRAMP space, I see a lot of mistakes cloud service providers (CSPs) make that cause them a tremendous amount of grief when seeking authorization. The process is painful enough on its own, but many of the people you hear venting frustration have made missteps.
Protecting Local Government Data: Why Password Managers Are Essential
Cyberthreats and ransomware attacks can be crippling for municipalities and county government offices. Local government employees need to access a growing number of systems, applications and databases to perform their duties, while the rise of remote work has drastically increased the attack surface of a typical small government office.
Becoming FedRAMP and StateRAMP Authorized - Part 1
Cloud-based applications and services are booming in 2023, in both the public and private sector. One of the largest and most sought-after clients for any tech company is the U.S. government. In fact, the federal government is investing billions of dollars annually in transitioning IT resources away from on-premises to secure and cost-effective commercial cloud services such as IaaS (infrastructure as a service), PaaS (platform as a service), and SaaS (software as a service).
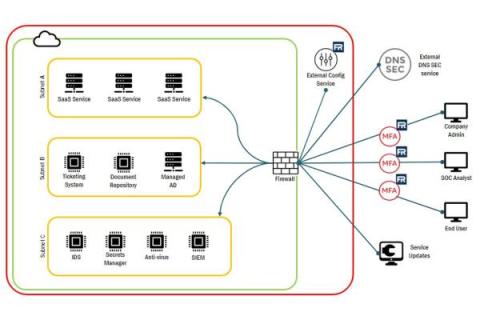
Understanding FedRAMP System Boundary
In the ever-changing world of technology, staying secure is a top priority for many organizations. Identifying and documenting system boundaries is essential for keeping data safe and secure, but what does this mean? In this article, we’ll explore FedRAMP System Boundary, how to identify them, and how to generate FedRAMP System Boundary diagrams.