Ultimate Protection: CyberArk Secure Browser & Proofpoint Anti-Phishing Integration | CyberArk
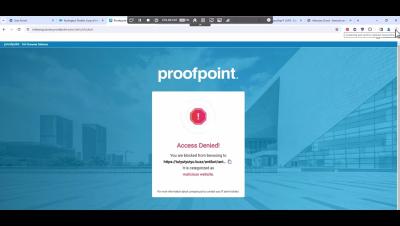
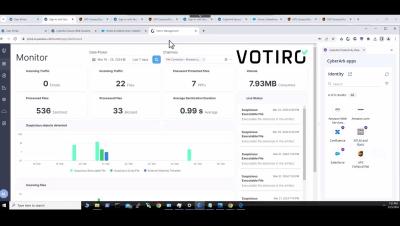
Discover the next level of web security with the CyberArk Secure Browser! In this video, we dive into the powerful features of CyberArk's Secure Browser, designed to provide: Granular Policy Controls Data Exfiltration Prevention Session Monitoring Credential Security Privacy Enforcement But that's not all! We also explore how combining CyberArk's Secure Browser with Proofpoint's industry-leading anti-phishing capabilities offers users comprehensive, real-time protection against phishing sites attempting to steal credentials and sensitive data.